As information technology continues to evolve, more and more people are penetrating cyberspace. Most organizations, companies, individuals, and even governments…
Mar 21, 2023Ravie LakshmananCyber Threat Intel / Vulnerability As many as 55 zero-day vulnerabilities were exploited in the wild in…
Thank you for joining! Access your Pro+ Content below. 21 March 2023 The risks of an imbalance in AI Share…
Director Jen Easterly of the Cybersecurity and Infrastructure Security Agency (CISA) said that new members will be joining the team….
Bugcrowd Security Flash – The Kaseya REvil Attack Explained Source link
The Clop ransomware gang claims to have attacked Saks Fifth Avenue on its dark web leak site. The cyber security incident is…
ForgeRock announced ForgeRock Enterprise Connect Passwordless, a new passwordless authentication solution that eliminates the need for users to interact with…
Ransomware gangs are becoming increasingly assertive and aggressive in their approaches to victims, resorting to high-pressure tactics including campaigns of…
Client-side path traversal vulnerability class explained – $6,580 GitLab bug bounty Source link
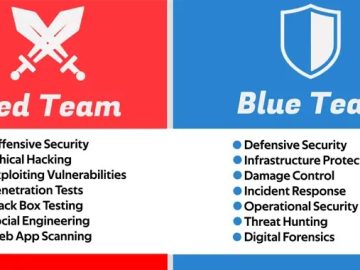
Security is a multifaceted field with multiple roles for carrying out diverse operations. In this article, we demystify the concept…
A threat actor recently contacted Ferrari S.p.A., an Italian luxury sports car manufacturer headquartered in Maranello, demanding a ransom for…
[ This article was originally published here ] This month, we asked women in the group to weigh in on…