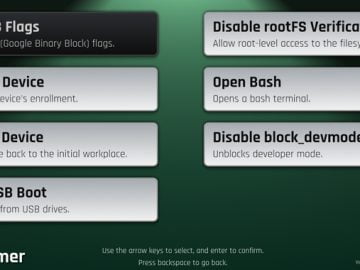
Feb 01, 2023Ravie Lakshmanan A new exploit has been devised to “unenroll” enterprise- or school-managed Chromebooks from administrative control. Enrolling…
Concerns about the cooling system setup in one of the datacentres used to host key healthcare systems for Guy’s and…
Microsoft has disabled multiple fraudulent, verified Microsoft Partner Network accounts for creating malicious OAuth applications that breached organizations’ cloud environments…
Printer exploit chain could be weaponized to fully compromise more than 100 models A security researcher dropped a zero-day remote…
Rogers’s last job for the government was leading teams within US Space Command that planned how and when to deploy…
GitHub announced that it suffered a security breach in which unauthorized individuals obtained access to specific development and release planning…
A few weeks back, Hackread.com reported about a malware-infected Android TV box available on Amazon: the T95 TV box. The…
[ This article was originally published here ] NEW YORK & DALLAS–()–, (BSA), a leader in cybersecurity advisory services and…
Help Net Security is in Israel this week for Cybertech Tel Aviv 2023, talking to the key players from the…
Feb 01, 2023Ravie LakshmananPayment Security / Risk The Brazilian threat actors behind an advanced and modular point-of-sale (PoS) malware known…
The UK Cyber Security Council and security professional association ISACA are to partner on a new audit and assurance scheme…
Horizon3 security researchers have released proof-of-concept (PoC) code for a VMware vRealize Log Insight vulnerability chain that allows attackers to…