The BianLian ransomware group has shifted its focus from encrypting its victims’ files to only exfiltrating data found on compromised…
By Ofer Klein, CEO and co-founder, Reco Recent research found that 96% of business leaders believe that effective communication is…
By PJ Rohall, Head of Fraud Strategy & Education – SEON It can be upsetting when you try to purchase…
Networking Fundamentals Source link
Project Zero, Google’s zero-day bug-hunting team, discovered and reported 18 zero-day vulnerabilities in Samsung’s Exynos chipsets used in mobile devices,…
Hey there, I hope you’ve been doing well! Pi Day In case you weren’t familiar, March 14th (3.14) was National…
Android malware ‘FakeCalls’ is circulating again in South Korea, imitating phone calls for over 20 financial organizations and attempting to…
The hacker claims that, among other sensitive data, the stolen information includes data about convicts, drug cartels, witnesses, and individuals…
The green tech revolution risks passing developing countries by without urgent intervention by the developed world, a report by the…
Webinar: Bug Bounty Q&A Source link
Cybercriminals are abusing Adobe Acrobat Sign, an online document signing service, to distribute info-stealing malware to unsuspecting users. The service…
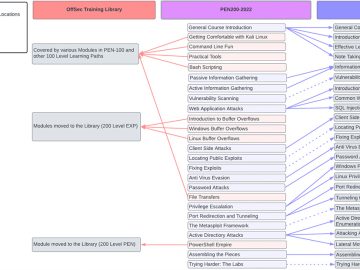
OffSec released the 2023 edition of Penetration Testing with Kali Linux (PEN-200). This new version, which incorporates the latest ethical…





![[tl;dr sec] #173 – What Software Will Be Post GPT-4, the Cybersecurity Landscape, Reducing Attack Surface in AWS [tl;dr sec] #173 - What Software Will Be Post GPT-4, the Cybersecurity Landscape, Reducing Attack Surface in AWS](https://image.cybernoz.com/wp-content/uploads/2023/03/tldr-sec-173-What-Software-Will-Be-Post-GPT-4-360x270.jpg)