A new global study has looked into how SOC’s go about protecting organisations from threats, where they focus the most…
Hornetsecurity launched VM Backup V9 – the newest version of its virtual machine (VM) backup, replication and recovery solution. This…
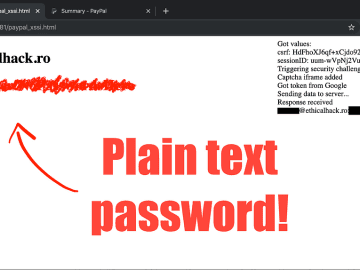
And Credit Card Number Too Continue reading on Medium » Source link
AWS has been offering Amazon Linux, a cloud-optimized Linux distribution, since 2010. This distribution’s latest version is now available. Amazon…
In last year’s edition of the Security Navigator we noted that the Manufacturing Industry appeared to be totally over-represented in…
HOW DID THIS HAPPEN!? (13370822 LHE VLOG) Source link
The failure of Silicon Valley Bank (SVB) on March 10, 2023, as a result of a bank run on its…
Unpatched vulnerabilities are responsible for 60% of all data breaches. The Department of Homeland Security has estimated that the proportion…
Mar 16, 2023Ravie LakshmananCyber Attack / Vulnerability Multiple threat actors, including a nation-state group, exploited a critical three-year-old security flaw…
Russian cybercriminals are offering sensitive information stolen from the US Marshals Service (USMS) for sale on the dark web. The…
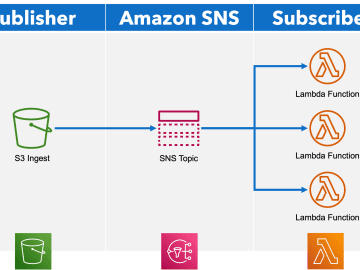
Note: This is the “text notes” version of my DEF CON 30 Cloud Village Lightning Talk. The talk was not…
Cyber attribution is a process by which security analysts collect evidence, build timelines and attempt to piece together evidence in…