The Transportation Security Administration (TSA) recently issued new cybersecurity requirements for the aviation industry, which follows last year’s announcement for…
I hacked Outlook and could’ve read all of your EMAILS! Source link
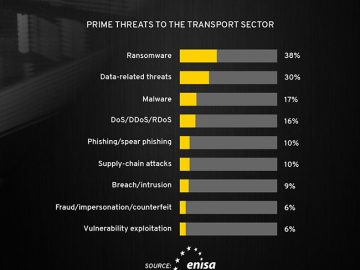
Between January 2021 and October 2022, the EU Agency for Cybersecurity (ENISA) analyzed and mapped the cyber threats faced by…
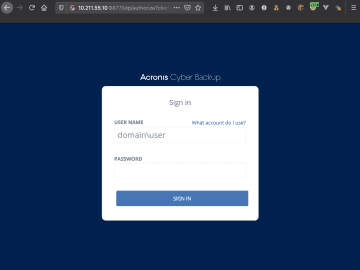
CVE-2020-16171: Exploiting Acronis Cyber Backup for Fun and Emails You have probably read one or more blog posts about SSRFs,…
An average enterprise storage and backup device has 14 vulnerabilities, three of which are high or critical risk that could…
Broken Access Control – Lab #8 UID controlled by parameter, with unpredictable UIDs | Long Version Source link
Don’t make random HTTP requests. Source link
A vulnerability in the Markup tool that comes pre-installed on Pixel phones allows anyone with access to the edited image…
Image credit: Senator James Paterson. Liberal senator James Paterson has urged the government to build trust and psychological safety mechanisms…
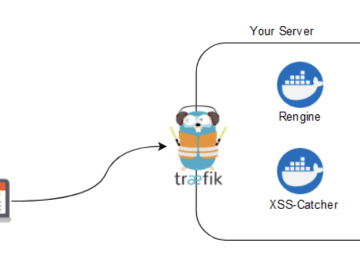
My bounty infrastructure with Docker [31/12/2020] : Updated the post for Rengine to v0.5 and a clearer / cleaner configuration…
WAN managers say they’re adopting zero trust security and using multiple infrastructure security vendors in response to the latest threats…
Compromised online stores have been injected with skimmers hiding around the Google Tag Manager script. We identified a new one…