MITRE launched its System of Trust risk model manager and established a community engagement group of 30 members. Expanding from…
Uber disclosed a bug submitted by zhero_: https://hackerone.com/reports/1790444 – Bounty: $650 Source link
Lions Gate Entertainment Corporation, doing business as Lionsgate, exposed users’ IP addresses and data on the content they saw on…
Over the last several years, endpoints have played a crucial role in cyberattacks. While there are several steps organizations can…
HTTP Fundamentals in 10 Minutes Source link
Self-hosted web administration solution CloudPanel was found to have several security issues, including using the same SSL certificate private key…
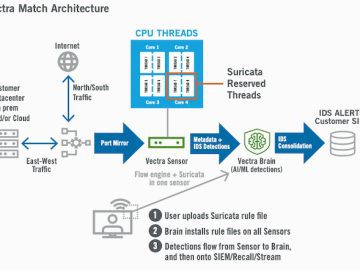
Vectra Match brings intrusion detection signature context to Vectra Network Detection and Response (NDR), enabling security teams to accelerate their…
The iStorage datAshur PRO² USB flash drive is one of a kind Source link
Microsoft is testing an updated version of the Windows 11 Snipping Tool that fixes a recently disclosed ‘Acropalypse’ privacy flaw…
According to Montenegro’s minister of interior Filip Adzic, Do Kwon was suspected of being “one of the most wanted fugitives.”…
We look at a current tax scam in circulation which looks to make an Emotet deposit on your PC. Tax…
Artwork by https://www.instagram.com/laracallejaillustrations/ Greetings! In this post I plan to outline some changes I’ve made to bugbountyhunter since launch and…