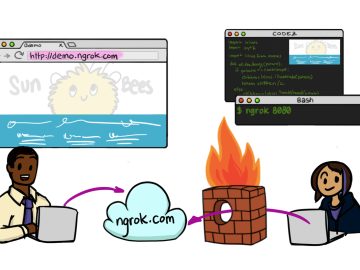
November 18, 2015 · security ngrok pentesting When gaining shell access to a machine on a network, a promising attack…
Pwn2Own Vancouver 2023 has ended with contestants earning $1,035,000 and a Tesla Model 3 car for 27 zero-day (and several…
The potential benefits of using artificial intelligence (AI) in weapons systems and military operations should not be conflated with better…
When PornHub launched their public bug bounty program, I was pretty sure that most of the low hanging fruits of…
In response to a recent vulnerability identified in Outlook, Microsoft recently published a proper guide for its customers to help…
A vulnerability in the redis-py open-source library was at the root of last week’s ChatGPT data leak, OpenAI has confirmed….
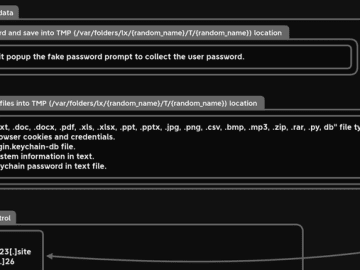
Mar 27, 2023Ravie LakshmananData Safety / Endpoint Security A new information-stealing malware has set its sights on Apple’s macOS operating…
The Confederation of British Industry (CBI) has launched a campaign to bolster support for the UK’s most innovative high-growth tech…
Over the last few years, usage of vulnerability disclosure and bug bounty programs have increased significantly. It is now almost…
The Australian consumer lender, Latitude Financial, has suffered a major cyber attack, leading to a data breach of passport and…
BEC attacks are usually aimed at stealing money or valuable information, but the FBI warns that BEC scammers are increasingly…
Mar 27, 2023The Hacker NewsSaaS Security Single sign-on (SSO) is an authentication method that allows users to authenticate their identity…