A previously unidentified Iranian threat actor has emerged with sophisticated social engineering tactics aimed at academics and foreign policy experts…
Working in the cyber security industry has always been high-pressure but we have seen that pressure intensify. Advancing threats, expanded…
Cisco became aware of a new attack variant against Secure Firewall ASA and FTD devices Pierluigi Paganini November 06, 2025…
The State of Nevada has published an after-action report detailing how hackers breached its systems to deploy ransomware in August,…
ValleyRAT has emerged as a sophisticated multi-stage remote access trojan targeting Windows systems, with particular focus on Chinese-language users and…
Role models are everywhere, and while Computer Weekly’s list of the Most Influential Women in UK Tech highlights the women…
Google sounds alarm on self-modifying AI malware Pierluigi Paganini November 06, 2025 Google warns malware now uses AI to mutate,…
North Korean threat actors are evolving their attack strategies by leveraging developer-focused tools as infection vectors. Recent security discoveries reveal…
“I set up a business called Enterprise Lab with two guys I met on Twitter,” says Naomi Timperley, who has…
ClickFix attacks have evolved to feature videos that guide victims through the self-infection process, a timer to pressure targets into…
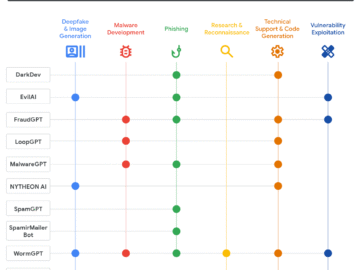
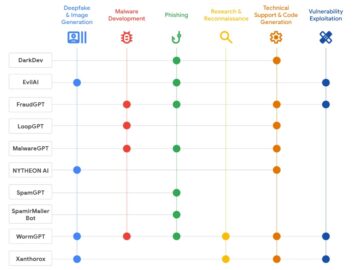
The cybercrime landscape has undergone a dramatic transformation in 2025, with artificial intelligence emerging as a cornerstone technology for malicious…
Security researchers have identified a sophisticated new malware family, Airstalk, that exploits VMware’s AirWatch API—now known as Workspace ONE Unified…