Hey there, I hope you’ve been doing well! Coffee Snobs Aficionados I’m not a big coffee person, but it seems…
The most interesting security related news from the week of March 20 – 26. Last week on Malwarebytes Labs: Stay…
I AM GIVING AWAY A CHROMEBOOK – 100k Twitter GiveAway Source link
Several security vulnerabilities were recently addressed by Canonical in both Graphviz and the Linux kernel of Ubuntu. Recent discoveries include…
A report compiled by Barclays states that the amount of money lost in romance scams has reached an average of…
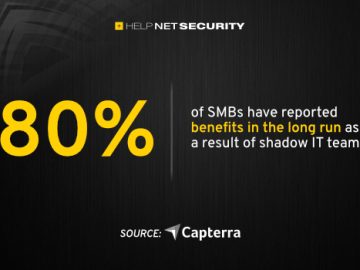
Shadow IT teams, also known as rogue IT teams, have grown in popularity in recent years due to the rise…
While Dole hasn’t said a lot about the February ransomware incident, it has revealed threat actors accessed employee data. Fruit…
8×8 disclosed a bug submitted by shriyanss: https://hackerone.com/reports/1825472 Source link
Cyberattacks tend to come from two angles: criminals take advantage of employees with privileged access or of security weaknesses in…
We look at a bogus Chat GPT Chrome extension which was after Facebook cookies. If you’re particularly intrigued by the current wave…
Mar 28, 2023Ravie LakshmananMobile Security Apple on Monday backported fixes for an actively exploited security flaw to older iPhone and…
Solving the Pickle Rick CTF Source link
![[tl;dr sec] #169 – Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS [tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS](https://image.cybernoz.com/wp-content/uploads/2023/03/tldr-sec-169-Top-10-Web-Hacking-Techniques-of-360x270.jpg)