Dubai / May 1st 2023 / Cyberpress — Cybersecurity gets a new dedicated newswire. , a press release distribution platform…
Discussions about the GDPR (General Data Protection Regulation) often touch upon security, a topic that few people know as well…
Seems like everyone, including me, is talking about how AI is going to take over everything. Cool, but what does…
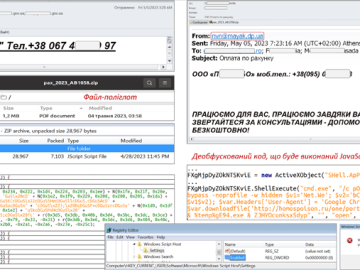
May 08, 2023Ravie LakshmananCyber Attack / Data Safety An ongoing phishing campaign with invoice-themed lures is being used to distribute…
This blog post was contributed by Slack Staff Technical Program Manager Branden Jordan. Given the success of Slack’s previous promotion…
It is not accurate to say that 5G networks are completely immune to cyber attacks. Like any other network, 5G…
A key term when discussing encryption these days is end-to-end (E2E) encryption. The idea with E2E encryption is that data…
Kerala Cyber Xtractors, a hacking group claiming to be from India, posted names of targets from Pakistan and Dhaka, Bangladesh….
We have released Detectify API v 2 to help you integrate Detectify with your own systems and make it your…
It is concerning to hear about the allegations and warnings issued by China’s National Computer Virus Emergency Response Centre (CVERC)…
Businesses worldwide are eagerly embracing the potential for AI to provide personalized customer experiences, but customers remain cynical, according to…
AI technology is fueling a rise in online voice scams, with just three seconds of audio required to clone a…