Server architecture can differ in a lot of ways, but the three main categories would be on-prem, cloud and serverless….
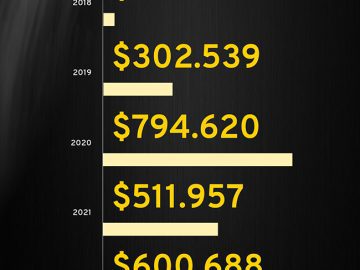
Companies that fail to protect their customers’ information are likely to face lawsuits in the year 2023, as impacted customers…
Organizations have strengthened security measures and become more resilient, but threat actors are still finding ways through, according to BakerHostetler….
May 02, 2023Ravie LakshmananVulnerability / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added three flaws to…
On 20 January, HackerOne’s CEO, Marten Mickos, sat down for a chat with European hacker, Julien Ahrens a.k.a @mrtuxracer, and…
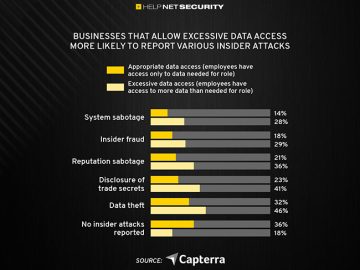
Insider attacks such as fraud, sabotage, and data theft plague 71% of U.S. businesses, according to Capterra. These schemes can…
EdOverflow is known for contributing a bunch of stuff: active in the community, one of the people behind security.txt –…
Since Google bought Android 2005, its sole responsibility has been to provide the best user experience and ensure security for…
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
Security analysts face the demanding task of investigating and resolving increasing volumes of alerts daily, while adapting to an ever-changing…
In this Help Net Security interview, Filipe Beato, Lead, Centre for Cybersecurity, World Economic Forum, shares his expertise on the…
We are excited to announce that we have partnered with TryHackMe to bring you Hacker Of The Hill (HoTH) on…