Recently, the cybersecurity researchers at eSentire have identified a shady piece of malware downloader, BatLoader, that has been engaged in…
Hopefully, you’ve been working with the Center for Internet Security (CIS) on securing your cloud infrastructure for a while now….
Ring, a popular home security company, has allegedly been the target of a data breach by the ALPHV ransomware group….
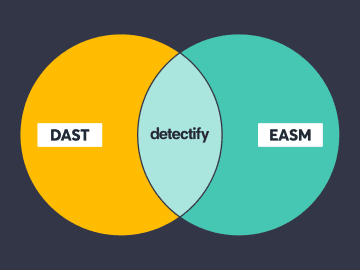
External Attack Surface Management (EASM) is the continuous discovery, analysis, and monitoring of an organization’s public facing assets. A substantial…
Offensive security released Kali Linux 2023.1 with new tools for purple and blue teamers for defensive security. On March 13th…
Managing user access in applications has always been a headache for any developer. Implementing policies and enforcing them can prove…
Mar 14, 2023Ravie LakshmananNetwork Security / Cyber Attack Government entities and large organizations have been targeted by an unknown threat…
There’s often a lack of understanding when it comes to DAST as a methodology versus DAST as a tool. How…
For the past 1 year or so, a museum is unable to access its artecraft database because of a ransomware…
Old ads can be startling—cigarette ads used to boast their health-giving properties, sugar-laden candy was once advertised as a dietary…
Warning FYI, I’ve had a report from someone else that this technique got their account temporarily locked. After changing their…
BEC attacks are growing year over year and are projected to be twice as high as the threat of phishing…