Plans are afoot to build a 250MW datacentre on the British overseas territory of Gibraltar by 2033 that its developers claim…
Throughout the past few years, APIs have become the backbone of digital infrastructure. They enable software-to-software communication, improve integration and…
A sophisticated malware campaign targeting macOS users has emerged, exploiting the widespread desire for free software to deliver the notorious…
A newly disclosed security flaw in pgAdmin4, the widely used open-source tool for managing PostgreSQL databases, has raised serious concerns among…
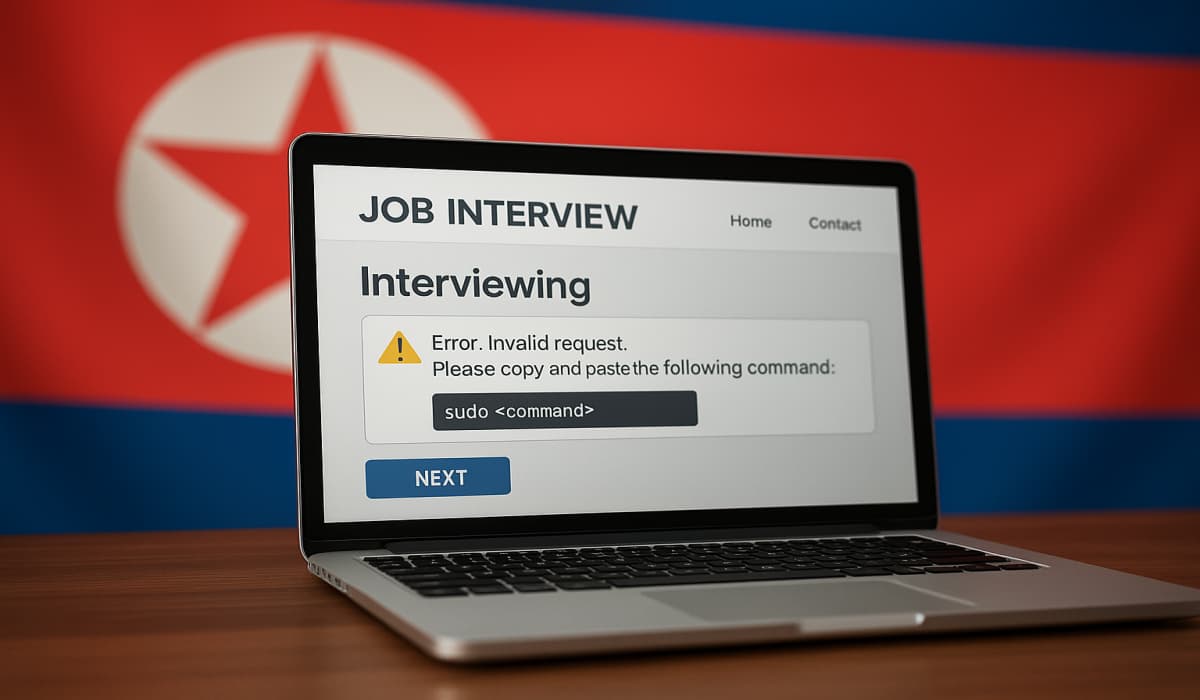
North Korea’s Lazarus Group uses the ClickFix scam in fake crypto job interviews to deploy malware, steal data, and fund…
The Pakistani government has launched an urgent investigation following reports of a massive data leak involving SIM holders’ personal information,…
A sophisticated supply-chain attack that impacted over 700 organizations, including major cybersecurity firms, has been traced back to a compromise…
When a security breach occurs, vital evidence often appears in unexpected places. One such source is Microsoft Azure Storage logs, which…
When Attackers Get Hired: Today’s New Identity Crisis What if the star engineer you just hired isn’t actually an employee,…
Chinese hackers, allegedly linked to the state, attempted to infiltrate the U.S. networks during sensitive trade discussions earlier this year…
Venezuela’s President Maduro said his Huawei Mate X6 cannot be hacked by US cyber spies Pierluigi Paganini September 08, 2025…
Microsoft’s Azure cloud platform is facing significant disruptions after multiple undersea fiber optic cables were severed in the Red Sea….