On September 2, 2025, a GitHub user known as Grommash9 committed a new workflow file to the FastUUID project. The…
A critical vulnerability has been discovered in Argo CD that allows API tokens with limited permissions to access sensitive repository…
The Biden administration considered spyware used to hack phones controversial enough that it was tightly restricted for US government use…
MeetC2 – A serverless C2 framework that leverages Google Calendar APIs as a communication channel Pierluigi Paganini September 06, 2025…
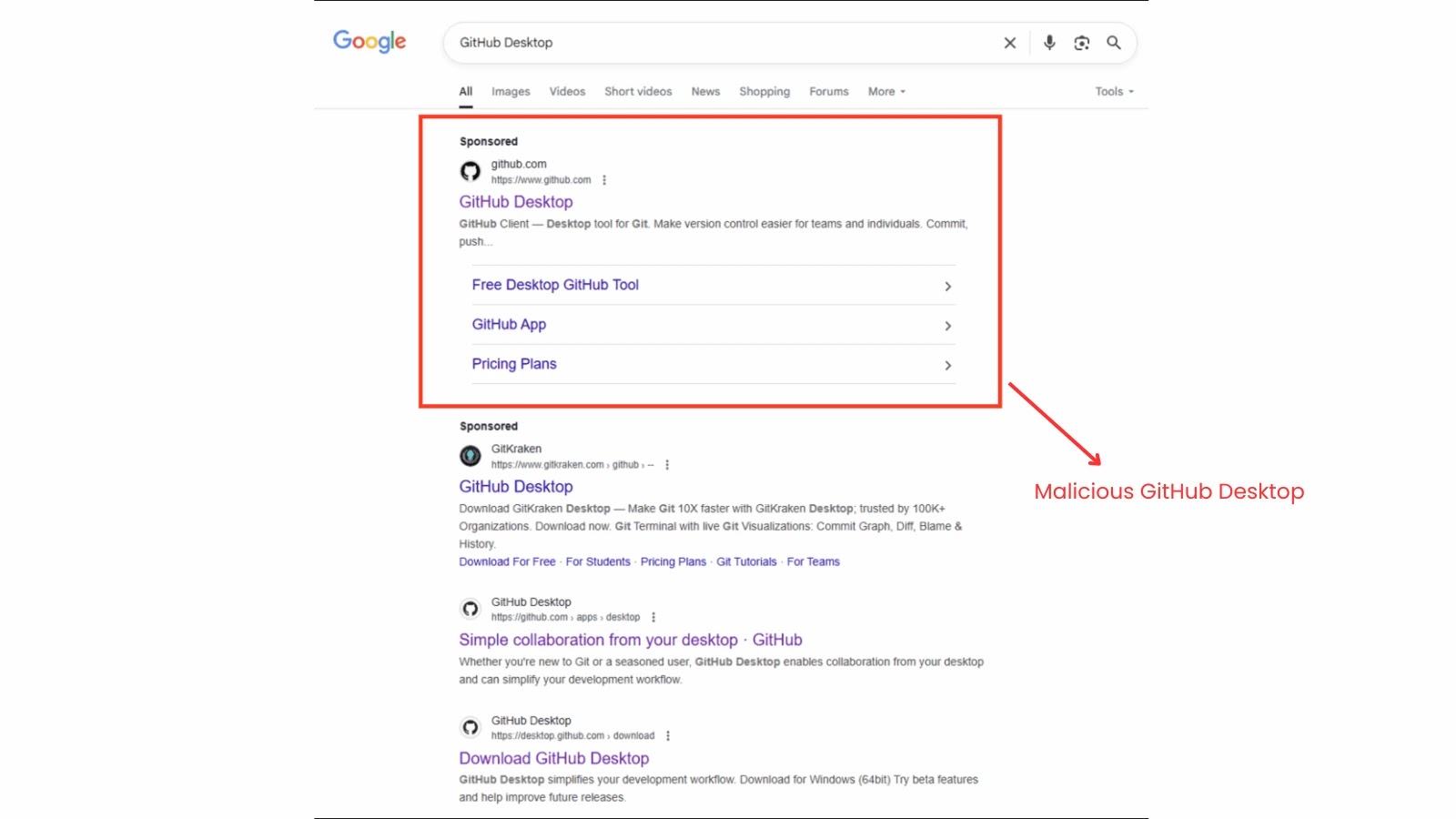
A sophisticated malware campaign, dubbed “GPUGate,” abuses Google Ads and GitHub’s repository structure to trick users into downloading malicious software….
Sep 06, 2025Ravie LakshmananSoftware Security / Cryptocurrency A new set of four malicious packages have been discovered in the npm…
As the attack surface expands and the threat landscape grows more complex, it’s time to consider whether your data protection…
Penetration testing and ethical hacking have been dominated by specialized Linux distributions designed to provide security professionals with comprehensive toolsets…
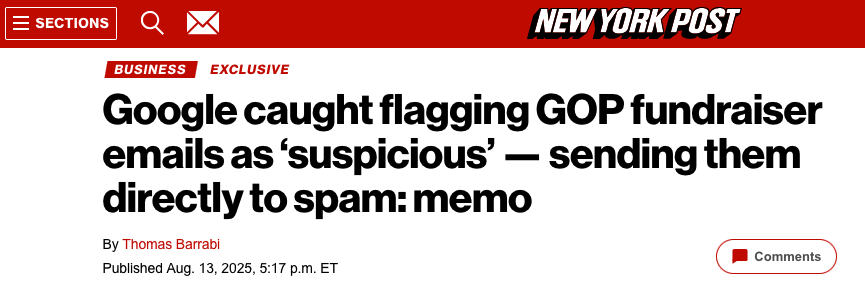
The chairman of the Federal Trade Commission (FTC) last week sent a letter to Google’s CEO demanding to know why…
There’s a popular argument going around that goes something like this: AI is a bubble Ok, maybe it’s useful and…
Bridgestone confirms a cyberattack that disrupted manufacturing plants. This article details the impact on employees, expert analysis, and a look…
There’s a popular argument going around that goes something like this: AI is a bubble It can be a bubble…