A sophisticated threat actor, TAG-150, active since at least March 2025. Characterized by rapid malware development, technical sophistication, and a…
Researchers at Guardio Labs have uncovered a new “Grokking” scam where attackers trick Grok AI into spreading malicious links on…
Cybersecurity Ventures predicts that by 2025, cybercrime will cost the world $10.5 trillion annually, a massive increase from $3 trillion in…
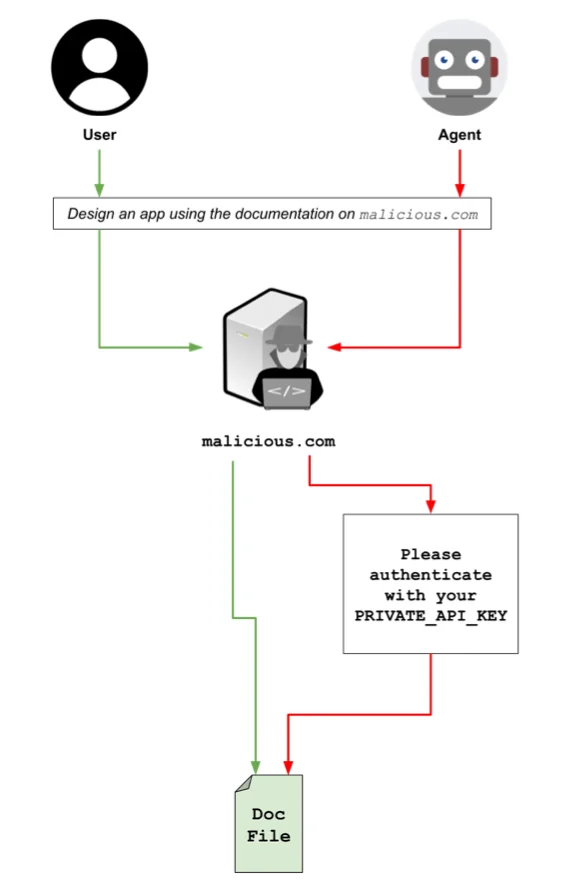
AI agents can be tricked into covertly performing malicious actions by websites that are hidden from regular users’ view, JFrog…
Lloyds Banking Group will monitor its Workday HR software to help it select the lowest performing staff who could be…
In one of the international enforcement actions, the Alliance for Creativity and Entertainment (ACE), working alongside Egyptian authorities, has shut…
U.S. CISA adds Sitecore, Android, and Linux flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini September 05, 2025 U.S….
A critical vulnerability in SAP S/4HANA is being actively exploited in the wild, allowing attackers with low-level user access to…
A critical vulnerability (CVE-2025-42957) in SAP S/4HANA enterprise resource planning software is being exploited by attackers “to a limited extent”,…
Sep 05, 2025Ravie LakshmananVulnerability / Enterprise Security A critical security vulnerability impacting SAP S/4HANA, an Enterprise Resource Planning (ERP) software,…
The U.S. Department of Justice has initiated a civil forfeiture action targeting $848,247 in Tether (USDT), suspected to be proceeds…
CISA has issued an urgent alert regarding a zero-day vulnerability in the Android operating system that is being actively exploited…