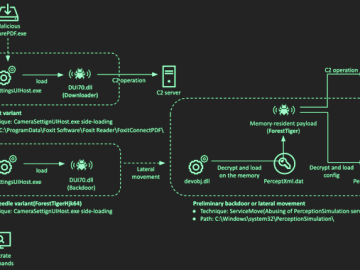
Apr 13, 2023Ravie LakshmananCyber Attack / Cyber Threat The North Korean threat actor known as the Lazarus Group has been…
The Information Commissioner’s Office (ICO) has welcomed the UK government’s proposals to regulate artificial intelligence (AI), but called for greater…
Guide to Entry Level Infosec Jobs Source link
URL validation bypass | Filedescriptor solves Intigriti’s XSS challenge Source link
It used to be that people were the greatest cybersecurity vulnerability, but this is no longer true. The rise of…
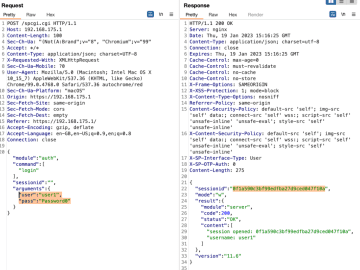
While my last finding affecting SecurePoint’s UTM was quite interesting already, I was hit by a really hard OpenSSL Heartbleed…
Broken Access Control – Lab #4 User role can be modified in user profile | Short Version Source link
XML External Entities (XXE) Explained Source link
Matt Atkinson | 05 July 2022 at 08:39 UTC If you use Burp Suite Professional or Burp Suite Community Edition…
Cloud Hacking: Common Attacks & Vulnerabilities Source link
Microsoft recently fixed a zero-day vulnerability that threat actors exploited to gain unauthorized privileges in the Windows Common Log File…
The Kodi Foundation learned that a dump of the Kodi user forum, MyBB software, was being sold on online forums. Kodi is…