The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding critical vulnerabilities in popular TP-Link router models…
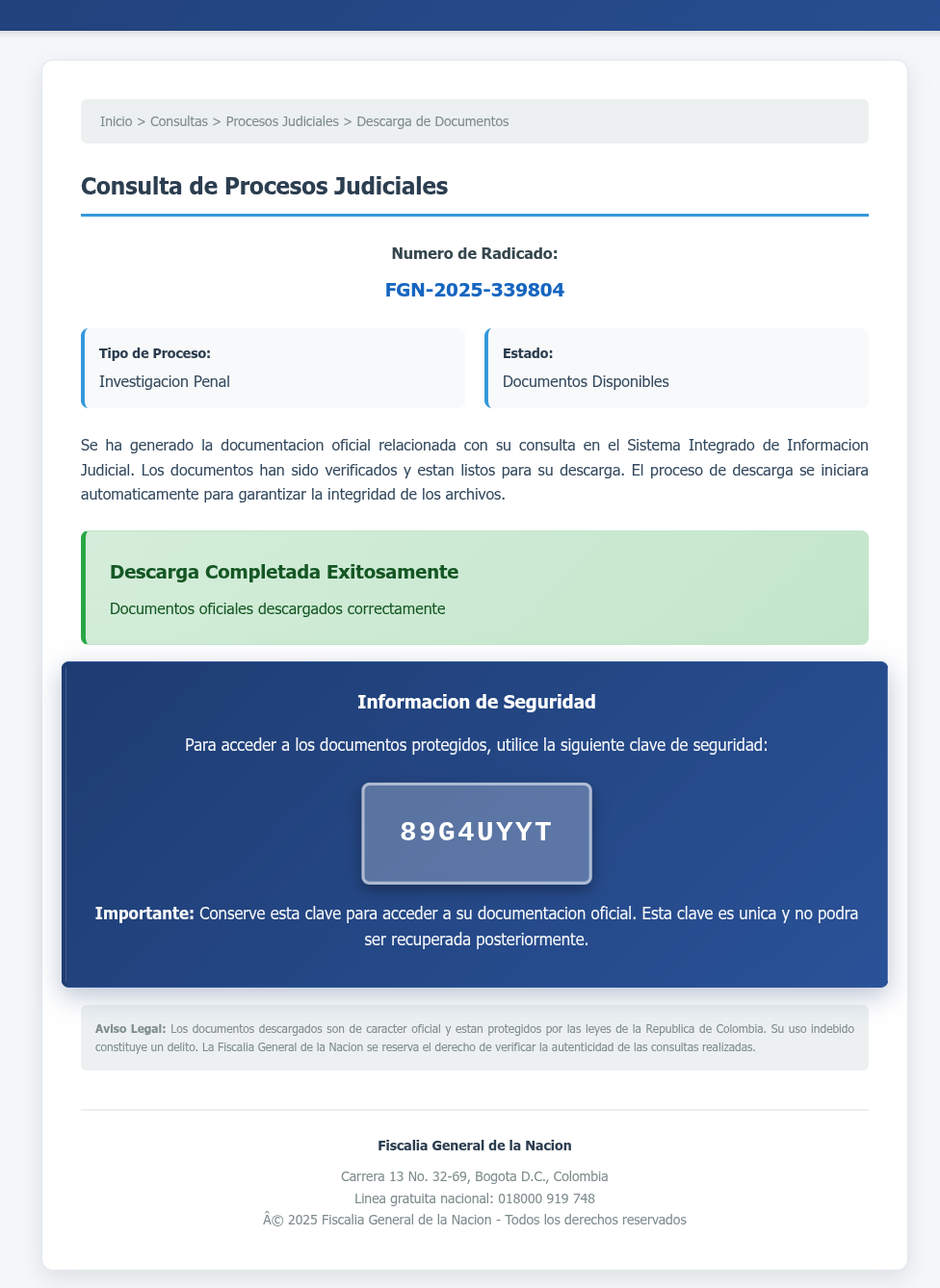
SVG files used in hidden malware campaign impersonating Colombian authorities Pierluigi Paganini September 05, 2025 VirusTotal uncovered an undetected malware…
A critical, zero-click vulnerability that allows attackers to hijack online accounts by exploiting how web applications handle international email addresses….
A sophisticated malware campaign targeting Colombian institutions through an unexpected vector: weaponized SWF and SVG files that successfully evade traditional…
Cybersecurity researchers have identified a sophisticated new command-and-control framework that exploits legitimate Google Calendar APIs to establish covert communication channels…
A sophisticated cryptojacking campaign that hijacks Windows’ native Character Map utility (“charmap.exe”) to evade Windows Defender and covertly mine cryptocurrency…
Security teams began observing a novel botnet strain slipping beneath the radar of standard Windows Defender defenses in early August…
A sophisticated North Korean cyber operation has been exposed, revealing how state-sponsored hackers systematically monitor cybersecurity intelligence platforms to detect…
Sep 05, 2025The Hacker NewsPentesting / Security Operations Pentesting remains one of the most effective ways to identify real-world security…
Czechia’s national cybersecurity watchdog has issued a warning about foreign cyber operations, focussed on Chinese data transfers and remote administration,…
A new technique that allows attackers to read highly sensitive files on Windows systems, bypassing many of the modern security…
A novel serverless command-and-control (C2) technique that abuses Google Calendar APIs to obscure malicious traffic inside trusted cloud services. Dubbed…