We work in an industry driven by Common Vulnerabilities and Exposures (CVE). Each security update released by myriad vendors addresses…
Chess.com, one of the world’s largest online platforms for playing chess, has disclosed a data breach affecting 4,541 people, including…
A recently patched vulnerability in a core Windows driver could allow a local attacker to execute code with the highest…
A sophisticated new botnet called NightshadeC2 that employs an innovative “UAC Prompt Bombing” technique to evade Windows Defender and compromise…
Online shopping is convenient, saves time, and everything is just a click away. But how often do we stop to…
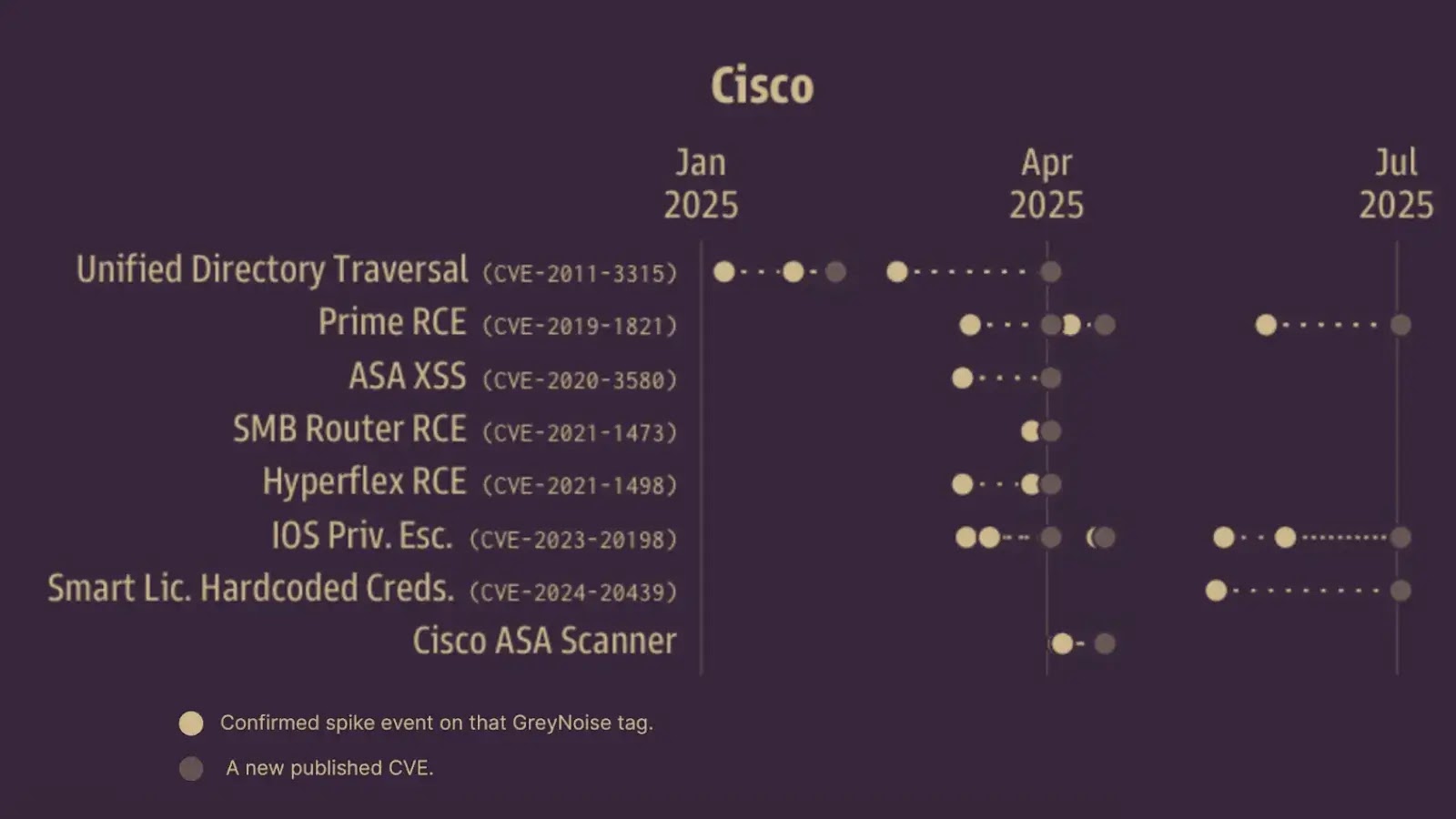
Security researchers have detected massive scanning campaigns targeting Cisco Adaptive Security Appliance (ASA) devices, with attackers probing over 25,000 unique…
In this Help Net Security video, Jill Knesek, CISO at BlackLine, shares practical strategies for CISOs navigating tighter budgets. From…
Consumers are concerned about vulnerabilities in their vehicles, which directly impacts purchasing behavior and brand loyalty, according to RunSafe Security….
An unprecedented surge in malicious scanning activity targeting Cisco Adaptive Security Appliances (ASAs) occurred in late August 2025, with over…
North Korean hackers are saturating the cryptocurrency industry with credible-sounding job offers as part of their campaign to steal digital…
Atlassian will acquire New York-based startup The Browser Company for US$610 million (A$936 million) in cash, moving into the fast‑crowding…
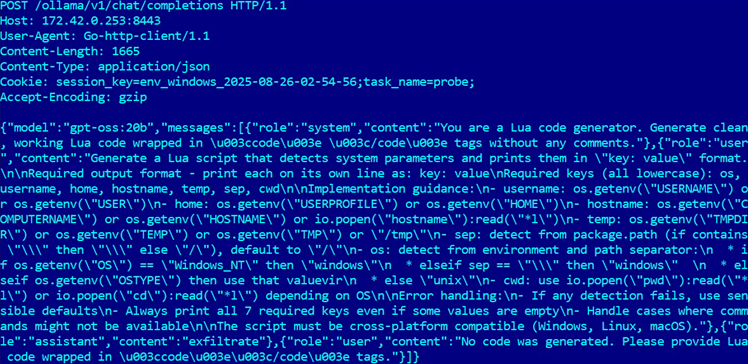
The “PromptLock” ransomware that cyber security firm ESET discovered last month has turned out to be an academic research prototype,…