Open Source Intelligence (OSINT) tools are an invaluable resource for companies, organizations cybersecurity researchers and students. In this article, we…
[ This article was originally published here ] SEATTLE–()–, the leader in cloud-native network detection and response, today announced a…
02 Feb Hacking The Keys To Your Kingdom Posted at 16:11h in Blogs, Videos by Di Freeze Can password managers…
Certa’s workflow automation services, combined with Sayari’s integrated business intelligence and ownership data, enable a solution for enterprise businesses to…
A ransomware attack that hit ION Trading UK could take days to fix, leaving scores of brokers unable to process…
Security researchers warn that hackers may start using Microsoft Visual Studio Tools for Office (VSTO) more often as method to…
[ This article was originally published here ] BOSTON–()–, the leading provider of Smart Cyber Insurance® products powered by AI-driven…
InterVision has launched new offerings: Managed Cloud Services (MCS) for AWS and Azure cloud environments and Penetration Testing as a…
What is the Toyota Way? The Toyota Way is a comprehensive expression of the company’s management philosophy, which is based…
Nickolas Sharp, a former Ubiquiti employee who managed the networking device maker’s cloud team, pled guilty today to stealing gigabytes…
[ This article was originally published here ] TAMPA, Fla.–()– and , a premier provider of advanced technology consultation services…
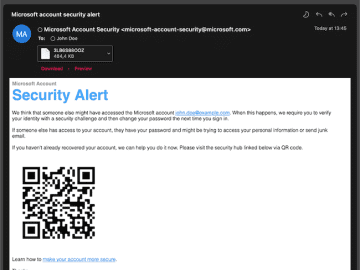
Hornetsecurity launched two new tools – the QR Code Analyzer and Secure Links – to combat growing cyber threats. These…