I hope you’ve been doing well! Gonna be Golden This past weekend I watched KPop Demon Hunters, and it was…
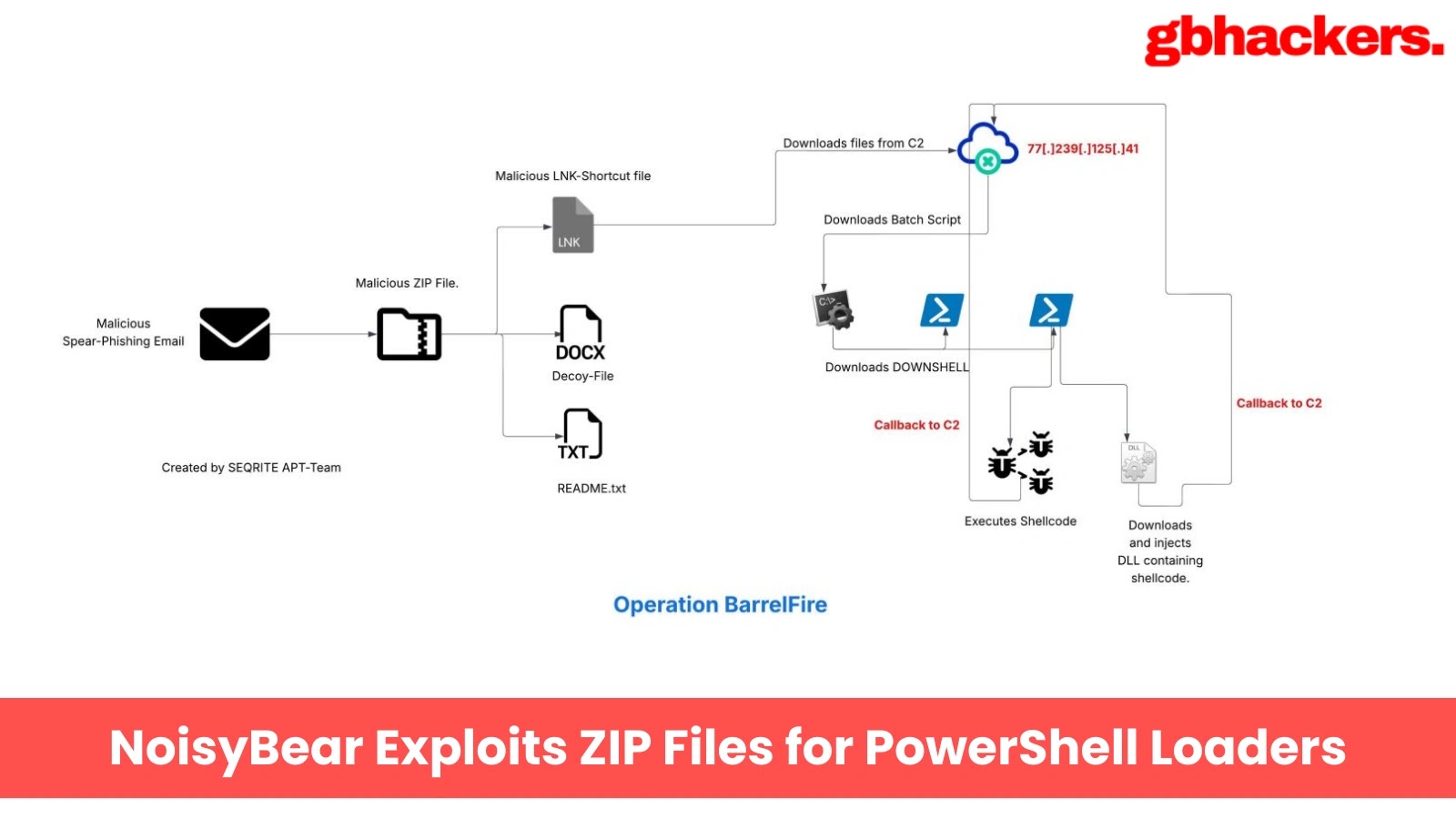
A sophisticated threat actor known as NoisyBear has emerged as a significant concern for Kazakhstan’s energy sector, employing advanced tactics…
ESET security researchers have uncovered a sophisticated cyber threat campaign targeting Windows servers across multiple countries, with attackers deploying custom…
Google has provided fixes for over 100 Android vulnerabilities, including CVE-2025-48543 and CVE-2025-38352, which “may be under limited, targeted exploitation.”…
The Cyber Express, in collaboration with Suraksha Catalyst, has officially released Episode 5 of the Black Hat USA 2025 CISO…
Car tire giant Bridgestone confirms it is investigating a cyberattack that impacts the operation of some manufacturing facilities in North America. The company believes…
The Django development team has issued critical security updates to address a high-severity vulnerability that could allow attackers to execute…
The threat actor known as NoisyBear has launched a sophisticated cyber-espionage effort called Operation BarrelFire, using specially designed phishing lures…
Darktrace reports new malware hijacking Windows Character Map for cryptomining, exposing risks of hidden attacks in everyday software processes. Cybersecurity…
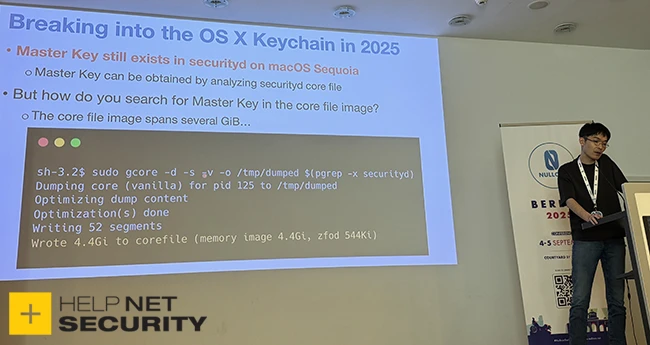
Today at Nullcon Berlin, a researcher disclosed a macOS vulnerability (CVE-2025-24204) that allowed attackers to read the memory of any…
Roblox is an online platform that allows users to build, play and share online worlds and 3D games. Unfortunately, it’s…
Listen to the article 9 min This audio is auto-generated. Please let us know if you have feedback. As food…
![[tl;dr sec] #295 – AI Code Analysis, AWS Detection Engineering, Anthropic Threat Intel Report [tl;dr sec] #295 - AI Code Analysis, AWS Detection Engineering, Anthropic Threat Intel Report](https://image.cybernoz.com/wp-content/uploads/2025/09/tldr-sec-295-AI-Code-Analysis-AWS-Detection-Engineering.png)