Here’s what to know about the malware with an insatiable appetite for valuable data, so much so that it tops…
Shadow IT leaves organizations exposed to cyberattacks and raises the risk of data loss and compliance failures 24 Oct 2025…
With cybersecurity talent in short supply and threats evolving fast, managed detection and response is emerging as a strategic necessity…
Here’s what to know about a recent spin on an insider threat – fake North Korean IT workers infiltrating western…
Microsoft has confirmed and issued a fix for a frustrating, long-running issue affecting Windows 10 and Windows 11 users in…
The Office of Personnel Management plans to collaborate on a “mass deferment” for a cyber scholarship-for-service program after the government…
Deepfakes are blurring the line between real and fake and fraudsters are cashing in, using synthetic media for all manner…
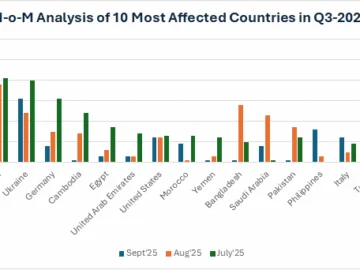
Hacktivist attacks on critical infrastructure doubled over the course of the third quarter, according to a new Cyble report. Hacktivist…
Families that combine open communication with effective behavioral and technical safeguards can cut the risk dramatically 30 Oct 2025 • …
The Balancer Protocol announced that hackers had targeted its v2 pools, with losses reportedly estimated to be more than $128…
From the end of Windows 10 support to scams on TikTok and state-aligned hackers wielding AI, October’s headlines offer a…
A remote access trojan dubbed SleepyDuck, and disguised as the well-known Solidity extension in the Open VSX open-source registry, uses an…