Security teams know, bug bounty hunters, and ethical hackers know it: Large attack surfaces are hard to manage. In this…
Microsoft says Rockstar Games has addressed a known issue affecting its launcher, causing the Red Dead Redemption 2 (RRD2) game…
Researchers from Kaspersky Labs uncovered a new wave of 3CX supply chain attacks targeting cryptocurrency companies to implant Gopuram. A…
When OpenAI released GPT-3 in July 2020, it offered a glimpse of the data used to train the large language model….
Western Digital (WD), a renowned manufacturer of Scandisk drives, has announced a data breach on its network, resulting in unauthorized…
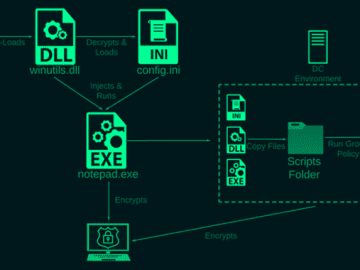
Apr 04, 2023Ravie LakshmananEncryption / Data Safety Cybersecurity researchers have taken the wraps off a previously undocumented ransomware strain called…
The UK’s newly created offensive cyber unit, the National Cyber Force (NCF), has carried out daily hacking operations to counter…
The post-pandemic era has seen a steep rise in cyberattacks. An analysis of cyber incidents revealed a 125% increase through…
Exploring the intersection of security, technology, and society—and what might be coming next… Standard Web Edition | April 3, 2023…
An ALPHV/BlackCat ransomware affiliate was observed exploiting three vulnerabilities impacting the Veritas Backup product for initial access to the target network. The…
Anonymous Sudan, a group of Hackers claiming to be as Palestinians, launched a distributed denial of service attack on Israel-based…
Clouded vision CTI systems are confronted with some major issues ranging from the size of the collection networks to their…