Network Visibility: The Silent Guardian of Cybersecurity Network complexity is killing enterprise security teams. Buried under mountains of configuration data,…
Sextortion-based hacking, which hijacks a victim’s webcam or blackmails them with nudes they’re tricked or coerced into sharing, has long…
Sep 03, 2025Ravie LakshmananMalware / Social Engineering Cybersecurity researchers have discovered two new malicious packages on the npm registry that…
Zero Trust: The Unsung Hero of Cybersecurity Cybersecurity professionals are drowning in complexity. Acronyms fly like digital confetti, vendors promise…
Israeli cybersecurity company Cato Networks has acquired AI security startup Aim Security in its first ever acquisition, reflecting the broader…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory warning about a critical vulnerability in SunPower PVS6…
The AI Threat Landscape: How Adaptive Security is Redefining Cyber Defense Cybersecurity professionals are facing an unprecedented challenge. The rise…
As organisations increasingly rely on cloud services to drive innovation and operational efficiency, chief information security officers (CISOs) face a…
Researchers at cyber security vendor Darktrace have unearthed what they say is the first documented case of NBMiner cryptomining malware…
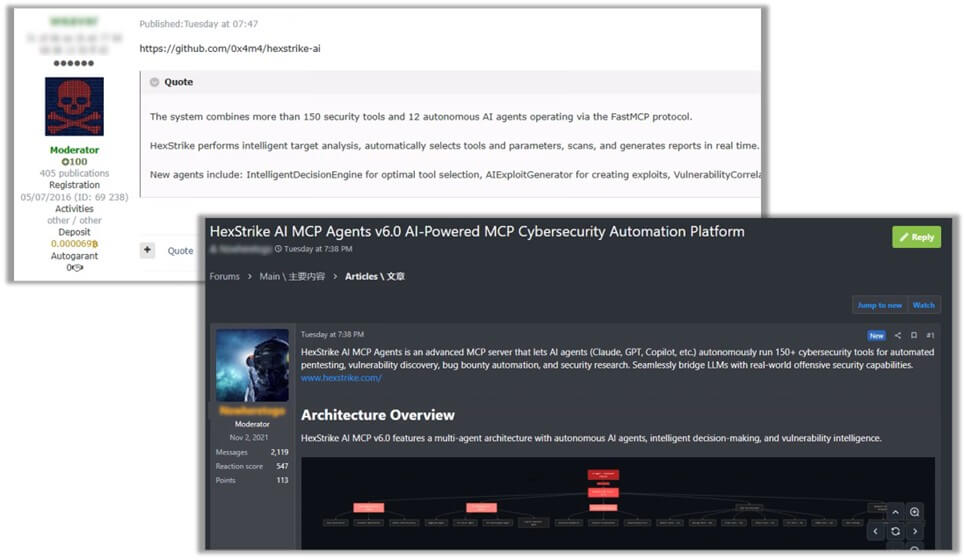
Crooks turn HexStrike AI into a weapon for fresh vulnerabilities Pierluigi Paganini September 03, 2025 Threat actors abuse HexStrike AI,…
Bane during the famous underground fight scene (click for full size) Not my normal type of content, obviously, but there’s…
Compiling an “ingredients list” for software can help organizations reduce cyber risks, avoid fines and save time, among other benefits,…