The volume of threat intelligence data has grown exponentially, but the ability to interpret and act on it has not….
A sophisticated phishing campaign has emerged, exploiting the trust placed in legitimate cloud hosting services. Threat actors are leveraging Cloudflare…
In this episode, Paulo Henrique speaks with Michael Fasulo, Senior Director of Portfolio Marketing at Commvault, about how organizations can…
Malwarebytes proudly topped three categories in PCMag’s 2025 Readers’ Choice Awards, recognized for exceptional protection and user satisfaction. We also earned the latest badge from AVLab Cybersecurity Foundation’s September “Advanced In-The-Wild…
Nov 03, 2025Ravie LakshmananCybercrime / Supply Chain Attack Bad actors are increasingly training their sights on trucking and logistics companies…
Android Apps misusing NFC and HCE to steal payment data on the rise Pierluigi Paganini November 03, 2025 Zimperium zLabs…
Supply chain attacks targeting the JavaScript ecosystem have evolved into sophisticated operations combining domain manipulation with social engineering. On September…
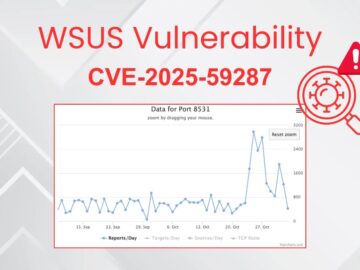
Security researchers at the SANS Internet Storm Center have detected a significant spike in suspicious network traffic targeting Windows Server…
In this episode, Paulo Henrique speaks with Michael Fasulo, Senior Director of Portfolio Marketing at Commvault, about how organizations can…
Global cybercrime costs were predicted by Cybersecurity Ventures to grow by 15 percent per year over the past five years—with malware…
Thirty-five accounting, finance and local government experts have signed an open letter to local government minister Steve Reed, calling for…
The Philippine National Police (PNP) stated on Monday that it is actively monitoring its online platforms and reinforcing defense against potential cyberattacks. The announcement…