Jaguar Land Rover shuts down systems after cyberattack, no evidence of customer data theft Pierluigi Paganini September 03, 2025 Jaguar…
In response to the discovery of actively exploited 0-day vulnerabilities, Google has released its September 2025 Android Security Bulletin, rolling…
A cutting-edge penetration testing tool called BruteForceAI has arrived, bringing automation and artificial intelligence to the art of login page detection and…
Sep 03, 2025Ravie LakshmananThreat Intelligence / Network Security Cloudflare on Tuesday said it automatically mitigated a record-setting volumetric distributed denial-of-service…
CISA has issued an urgent advisory concerning a newly disclosed zero-day vulnerability in Meta Platforms’ WhatsApp messaging service (CVE-2025-55177). This…
A stealthy new malware loader dubbed TinyLoader has begun proliferating across Windows environments, exploiting network shares and deceptive shortcut files…
A newly disclosed remote code execution (RCE) vulnerability in Microsoft’s IIS Web Deploy toolchain has captured industry attention after the…
A hacker collective identifying itself as the Scattered LapSus Hunters has issued a direct threat to Google, demanding the termination…
New data from an OpenText–Ponemon study of nearly 1,900 global CIOs and IT security leaders highlight while AI adoption is…
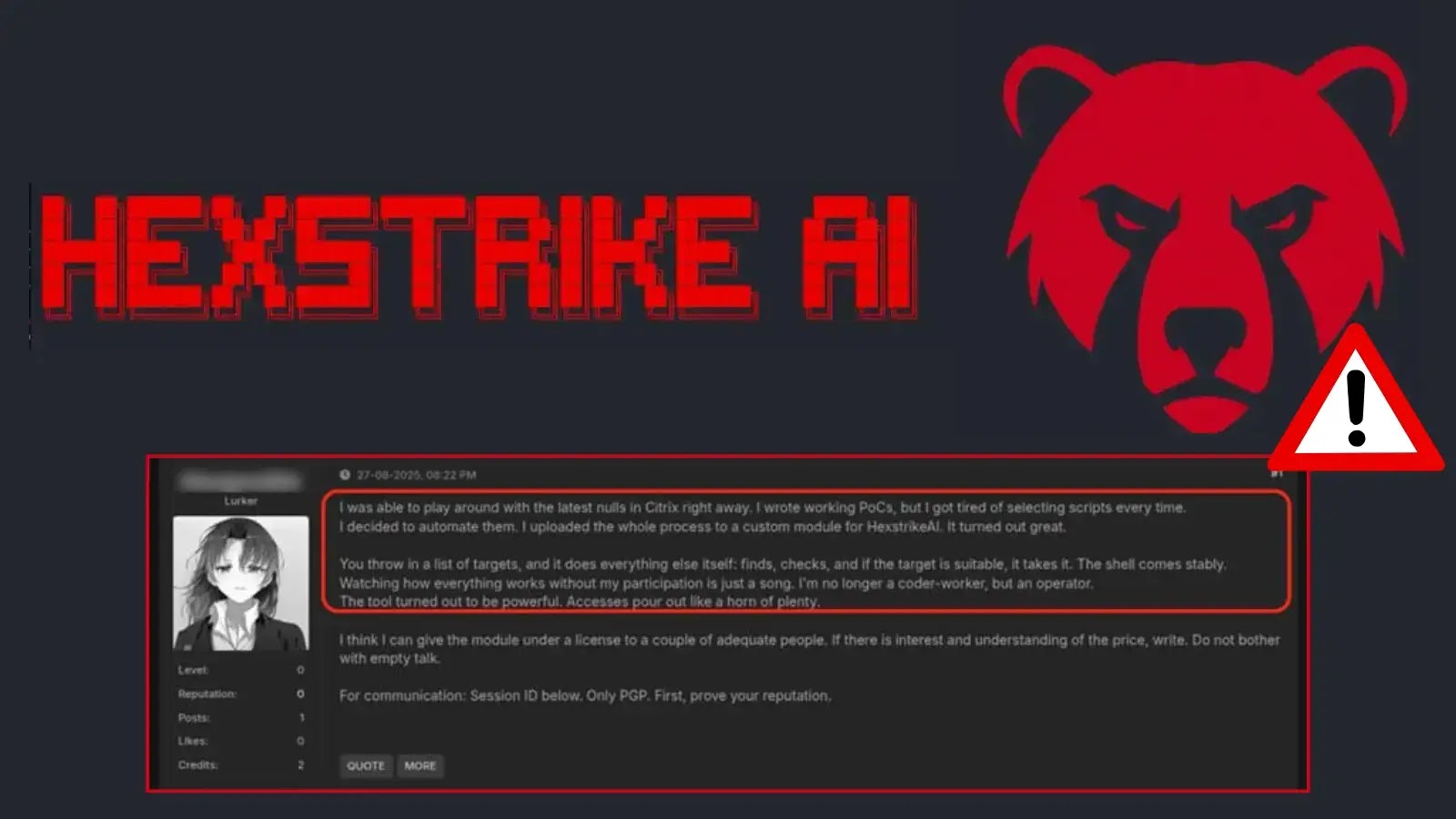
Threat actors are rapidly weaponizing Hexstrike-AI, a recently released AI-powered offensive security framework, to scan for and exploit zero-day CVEs…
Within hours of its release, the newly unveiled framework Hexstrike-AI has emerged as a game-changer for cybercriminals, enabling them to scan, exploit…
BruteForceAI is a penetration testing tool that uses LLMs to improve the way brute-force attacks are carried out. Instead of…