Abstract: Technological developments make it easier for people to communicate and share information. Facebook Messenger is an instant messenger that…
The AI Bill of Rights, bias, and operational challenges amid tightening budgets are pressing issues affecting the adoption of ML…
Mar 03, 2023Ravie LakshmananEnterprise Security / IoT A pair of serious security defects has been disclosed in the Trusted Platform…
Newham Council has revealed plans to set up a “data campus” at East Ham Town Hall, with the facility intended to…
US-based firearms business Central Missouri Machine Guns (CMMG) Inc was allegedly attacked by BlackCat ransomware gang. The ransomware gang listed…
The cybersecurity incident at the Netherlands-based geriatric healthcare service provider Attent Zorg Behandling turned out to be a ransomware attack,…
If you suspect your computer has been hacked, the first thing that comes to your mind is how to clean…
A new plug-in, created by Microsoft and MITRE, integrates various open-source software tools to aid cybersecurity professionals in bolstering their…
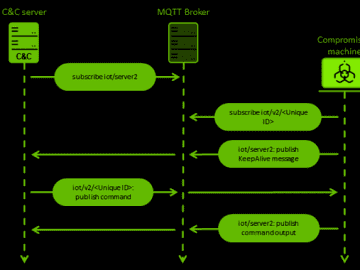
Mar 03, 2023Ravie LakshmananThreat Intelligence / Cyber Attack The China-aligned Mustang Panda actor has been observed using a hitherto unseen…
In recent years, we have witnessed increasing vulnerabilities in UEFI systems. This is alarming because these vulnerabilities have been patched…
While there was a reduction in the widespread exploitation of new vulnerabilities in 2022, the risk remains significant as broad…
Known vulnerabilities – those for which patches have already been made available – are the primary vehicle for cyberattacks, according…