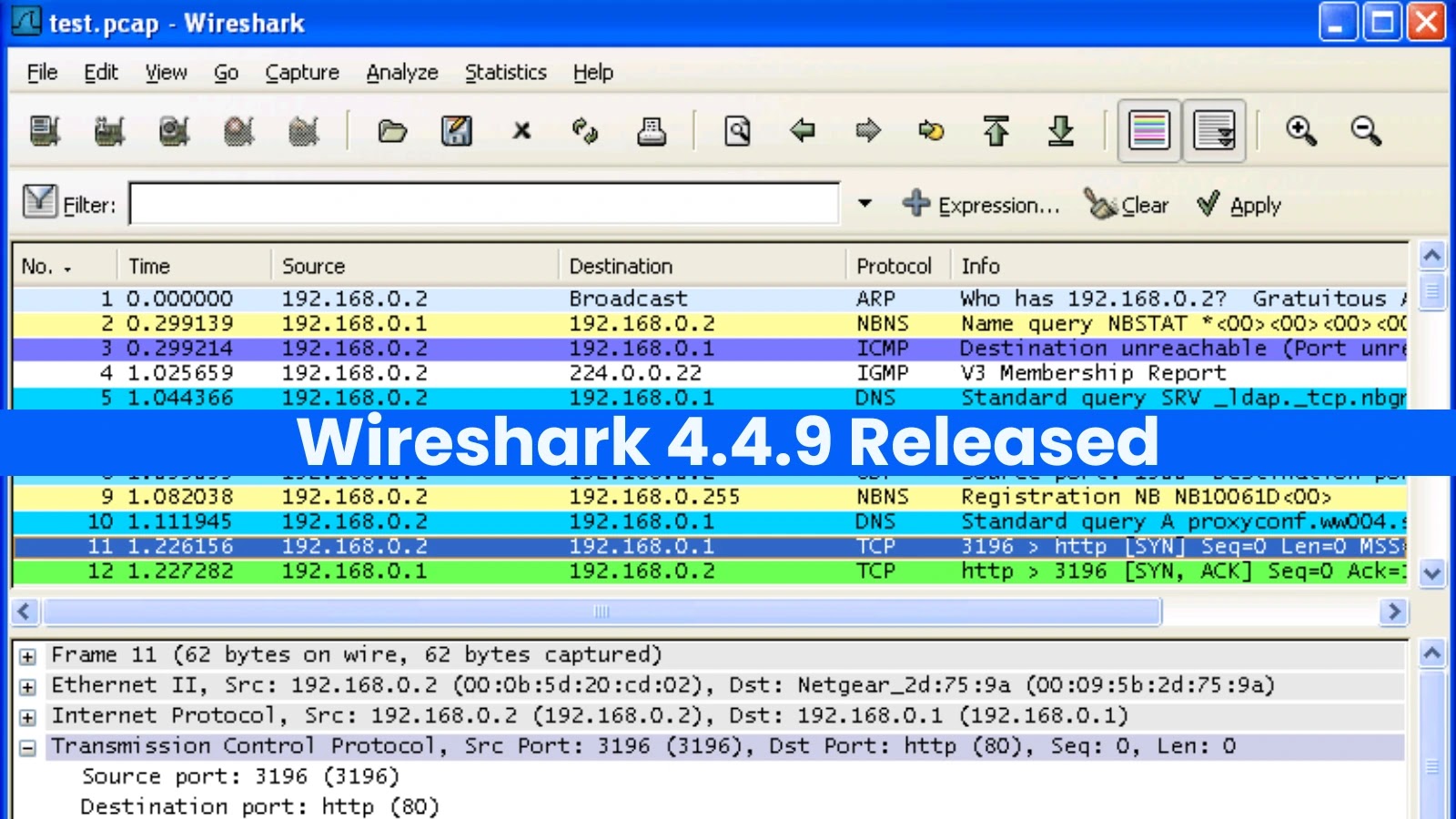
The Wireshark team has rolled out version 4.4.9, a maintenance release for the world’s most popular network protocol analyzer. This…
A sophisticated malvertising campaign has emerged that specifically targets hoteliers and vacation rental operators by impersonating well-known service providers. Okta…
Researchers have disrupted an operation attributed to the Russian state-sponsored threat group Midnight Blizzard, which sought access to Microsoft 365 accounts…
The telecommunications landscape is facing an unprecedented crisis as SIM swapping attacks surge to alarming levels, with the United Kingdom…
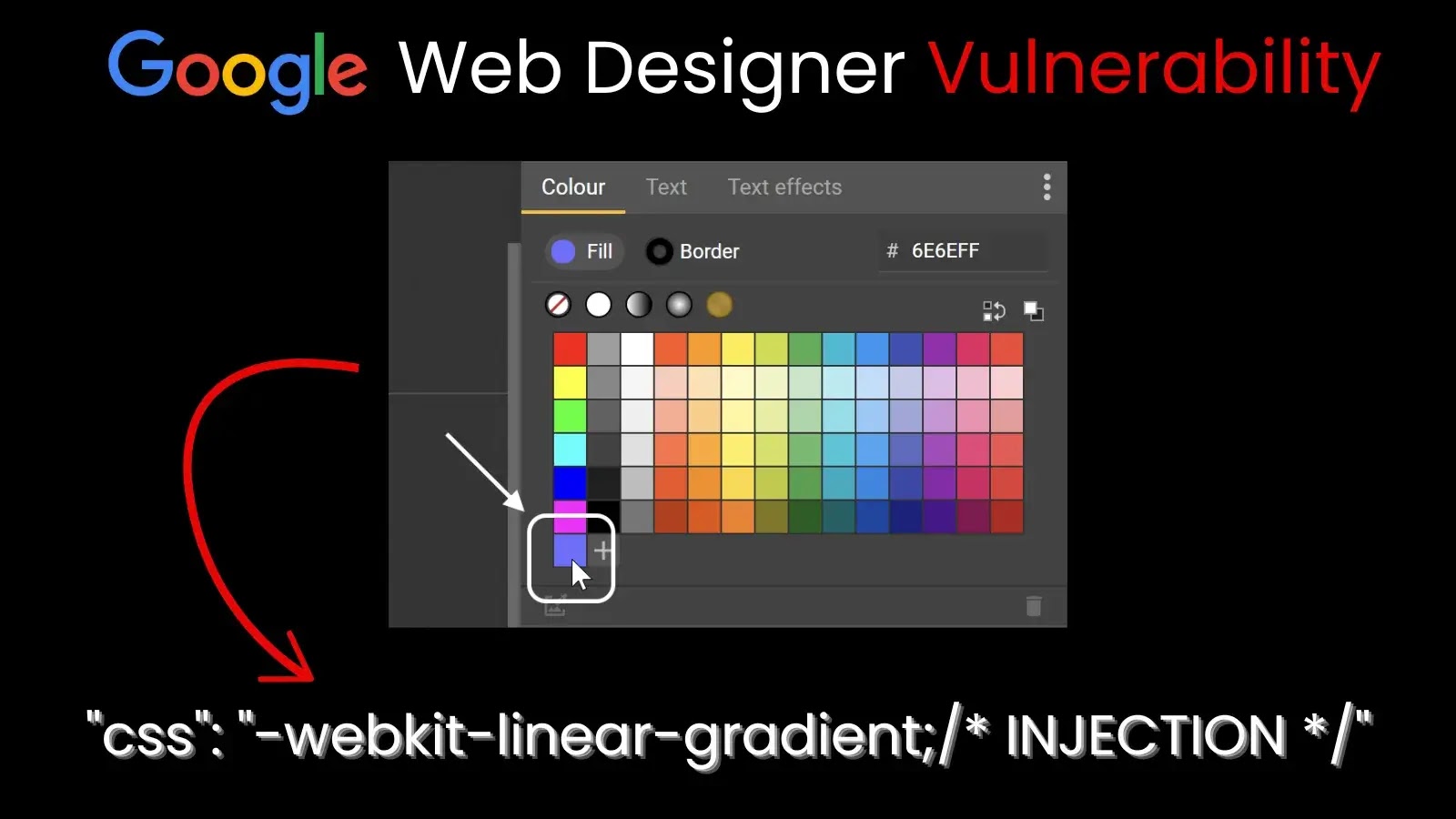
A critical client-side remote code execution (RCE) vulnerability in Google Web Designer exposed Windows users to full system compromise, according…
If you use ChatGPT to learn new topics, you might want to try its new flashcard-based quiz feature, which can…
Microsoft is issuing a direct call to its hardware partners, urging original equipment manufacturers (OEMs) to address configuration issues that…
Introduction: Addressing the Unavoidable Nature of Cyber Risk In a rapidly evolving cyber threat landscape, the need for sophisticated and…
Criminal IP, the AI-powered threat intelligence and attack surface management (ASM) platform developed by AI SPERA, announced its official entry…
Two step verification is the name Meta uses for what is generally referred to as Two-factor authentication (2FA). 2FA is…
Anthropic is planning to bring the famous Claude Code to the web, and it might be similar to ChatGPT Codex,…
In a significant security move, Microsoft announced on August 26, 2025, that it will require mandatory multifactor authentication (MFA) for…