Cohesity has appointed James Eagleton as Managing Director for Australia and New Zealand (ANZ). In this role, Eagleton will be…
Cybercriminals are now weaponizing Windows Defender Application Control (WDAC) policies to disable Endpoint Detection and Response (EDR) agents en masse….
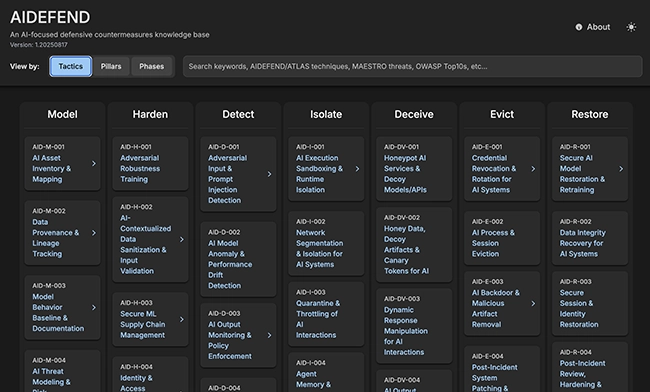
AIDEFEND (Artificial Intelligence Defense Framework) is an open knowledge base dedicated to AI security, providing defensive countermeasures and best practices…
A critical security vulnerability has been discovered in the Linux UDisks daemon that could allow unprivileged attackers to gain access…
The cybersecurity landscape has witnessed a dangerous evolution as Advanced Persistent Threat (APT) groups increasingly weaponize opportunistic infostealer malware for…
A team of researchers from Frondeur Labs, DistributedApps.ai, and OWASP has developed a new machine learning framework designed to help…
The Cybersecurity and Infrastructure Security Agency (CISA) has published nine Industrial Control Systems (ICS) advisories on August 28, 2025, detailing…
Red Hat has disclosed a critical security flaw in the Udisks daemon that allows unprivileged users to exploit an out-of-bounds…
Boards of directors are being told that cybersecurity is now central to business resilience and growth, and that they must…
There is constant pressure on security leaders to decide which controls deserve the most attention and budget. A new study…
Prompt injection attacks have emerged as one of the most critical security vulnerabilities in modern AI systems, representing a fundamental…
Two public hospital doctors have been arrested in Hong Kong for allegedly leaking patient information, the Post has learned. While…