On August 28, 2025, the Hikvision Security Response Center (HSRC) issued Security Advisory SN No. HSRC-202508-01, detailing three critical vulnerabilities…
When it comes to cybercrime, the stories are often told in numbers. By 2025, it is expected to cost $10.5 trillion…
The Securities and Exchange Board of India (SEBI) issued a clarification on Thursday regarding the scope and applicability of its…
Continue reading online to avoid the email cutoff issue > SECURITY | AI | MEANING :: Unsupervised Learning is a…
Over the past year, security researchers have observed a growing trend of North Korean–linked developers establishing credible-looking profiles on popular…
Virustotal today unveiled a powerful addition to its Code Insight suite: a dedicated API endpoint that accepts code snippets—either disassembled…
Aug 29, 2025The Hacker NewsEnterprise Security / Artificial Intelligence Generative AI platforms like ChatGPT, Gemini, Copilot, and Claude are increasingly…
It’s easy to overlook meeting audio quality. After all, it’s just one small detail in the long list of technologies…
I think Trump’s conviction might be the American Left’s version of Brexit. Let me explain. First off, I think Trump…
Cybersecurity researchers have uncovered a sophisticated malvertising campaign on Meta’s Facebook platform in recent weeks that targets Android users with…
A widespread supply chain attack on the popular Nx build system has compromised dozens of high-traffic packages, exposing sensitive credentials…
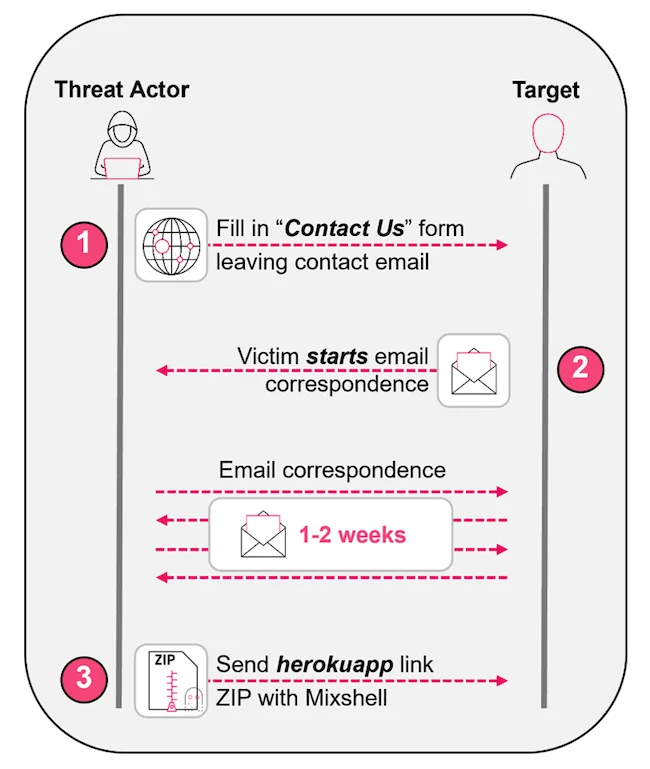
A recently uncovered phishing campaign – carefully designed to bypass security defenses and avoid detection by its intended victims –…