The SpaceX public offering date has generated considerable interest among investors and market observers. Scheduled for December 31, 2026, this…
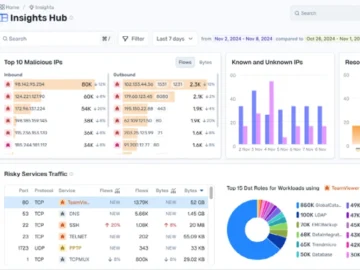
Illumio unveiled its solution to deliver agentless visibility and breach containment across both data center and cloud environments. Illumio Insights…
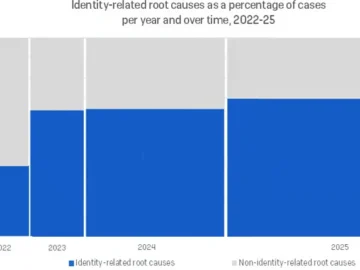
Cybersecurity governance is moving to the highest levels of organizational leadership, a shift highlighted by the European Union’s NIS2 Directive and Ireland’s…
The UK government is tightening its government cyber security posture with a dual strategy, faster vulnerability remediation and a long-term…
ManoMano data breach impacted 38 Million customer accounts Pierluigi Paganini February 27, 2026 European DIY platform ManoMano suffered a data…
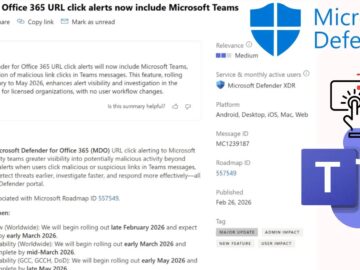
Microsoft Defender URL Alert Teams Microsoft is strengthening its cybersecurity ecosystem by extending Microsoft Defender for Office 365 (MDO) URL…
Trend Micro has disclosed eight security vulnerabilities in its Apex One endpoint protection platform, including two critical-severity flaws that allow…
Intrusions continue to center on credential access and timed execution outside standard business hours. The Sophos Active Adversary Report 2026…
How AI Aids Incident Response: Why Humans Alone Cannot Do IR Efficiently Pierluigi Paganini February 27, 2026 AI accelerates incident…
A major networking vendor has issued an out-of-cycle security bulletin to address a critical vulnerability in its Junos OS Evolved…
Malicious actors are abusing Go’s open-source ecosystem by deploying a backdoored crypto module that steals passwords and installs a Rekoobe…
Apple confirmed that the iPhone and iPad have been approved for use with classified information in NATO restricted environments. The…