The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert after detecting active exploitation of a critical zero-day…
The U.S. State Department in collaboration with Japan, South Korea, and private cybersecurity partners met in Tokyo, last week, to…
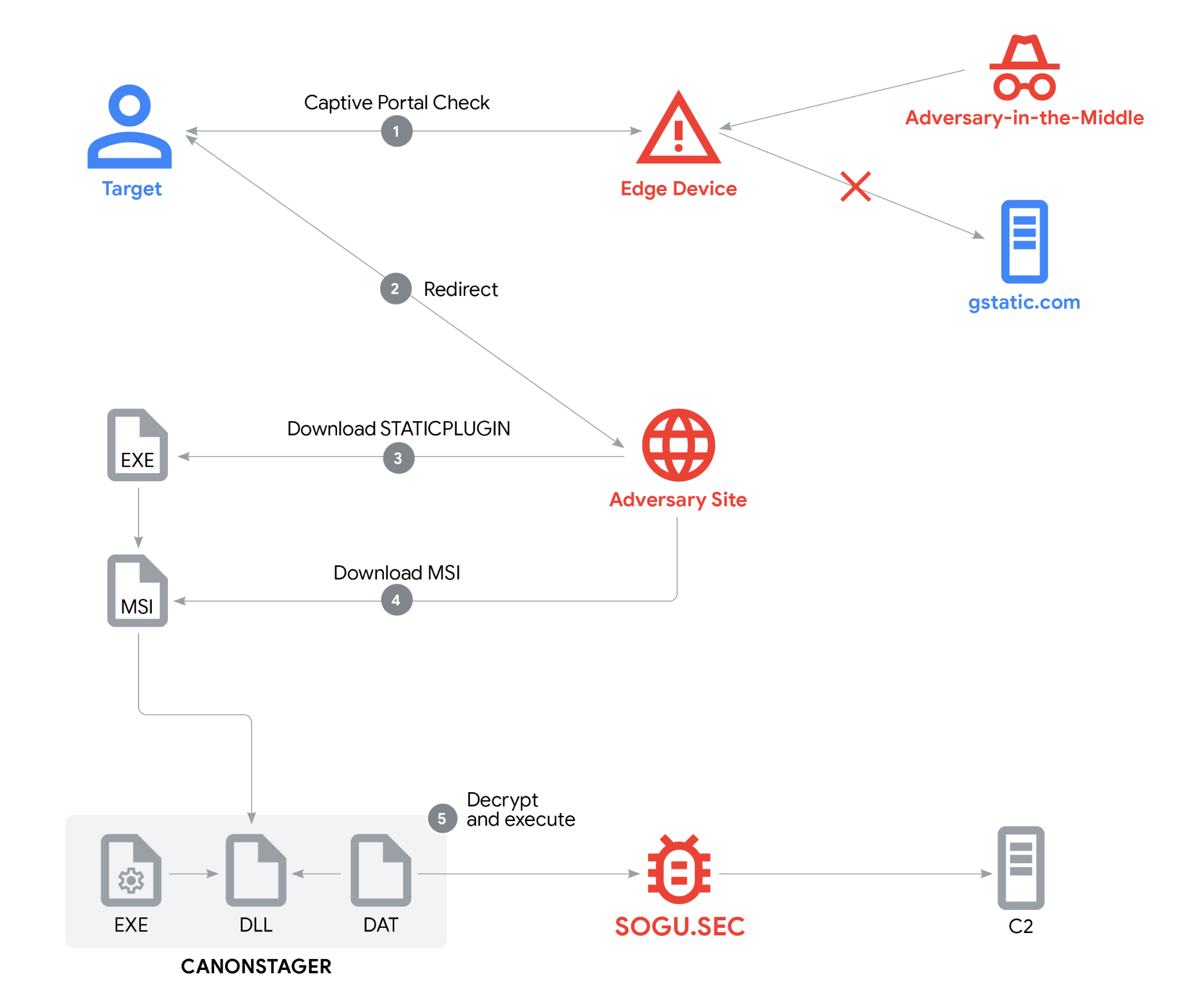
China linked UNC6384 targeted diplomats by hijacking web traffic Pierluigi Paganini August 27, 2025 The China-linked APT group UNC6384 targeted…
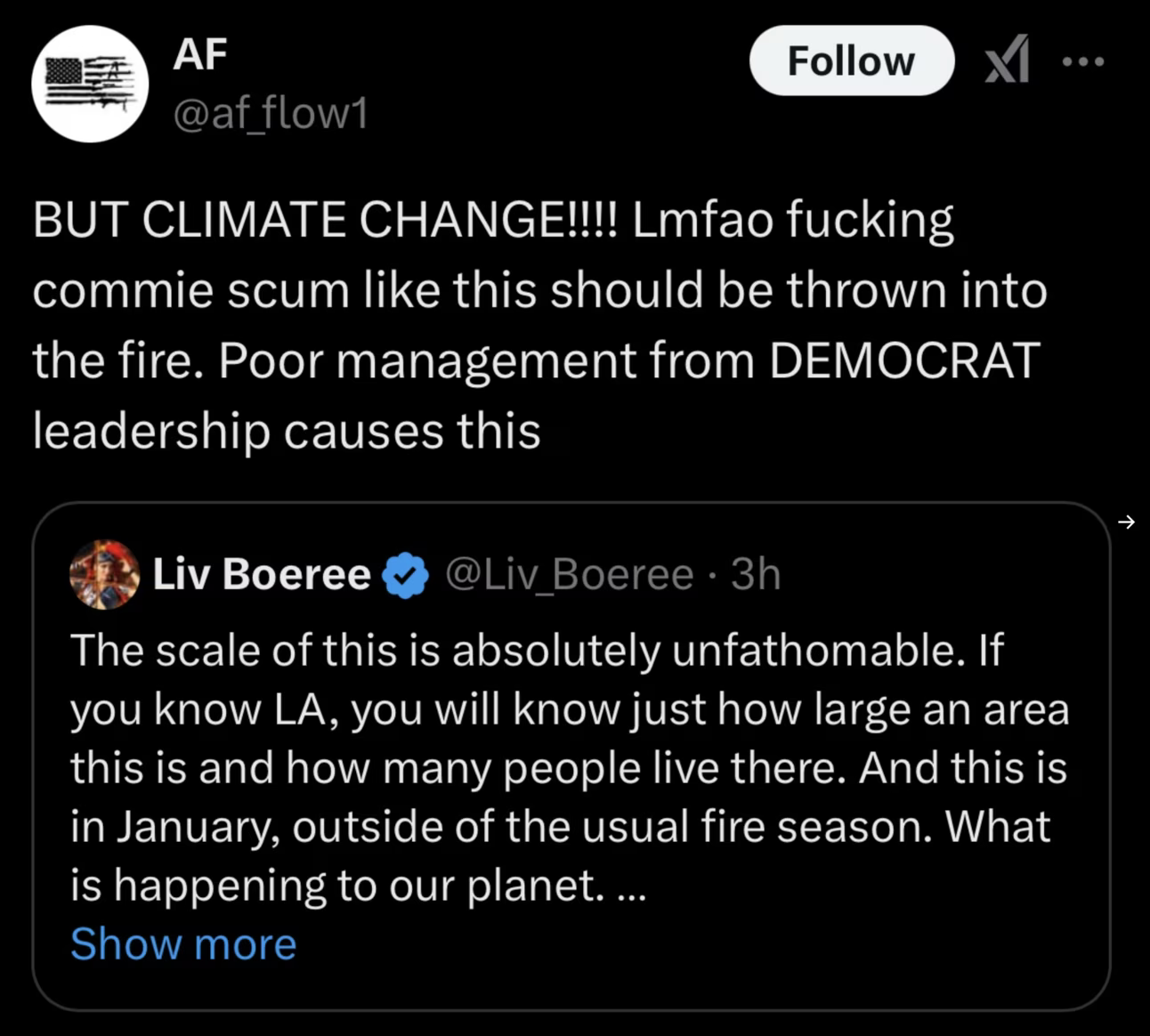
I clearly see the merits of both sides, similar to the end-to-end encryption discussion. The last few years have given…
Cybersecurity researchers at Truesec have uncovered a sophisticated malware campaign distributing a weaponized PDF editor under the guise of “AppSuite…
UNC6395 targets Salesloft in Drift OAuth token theft campaign Pierluigi Paganini August 28, 2025 Hackers breached Salesloft to steal OAuth/refresh…
Neovim command sequences visualization (click for full size) After returning to Neovim recently, I’ve discovered some powerful techniques for manipulating…
Over the past year, a shadowy threat actor known as TAG-144—also tracked under aliases Blind Eagle and APT-C-36—has intensified operations…
A recent investigation has uncovered that relying solely on large language models (LLMs) to generate application code can introduce critical…
The Keeling Curve shows atmospheric CO2’s relentless rise (click for full size) In 1958, Charles David Keeling began measuring atmospheric…
A newly disclosed vulnerability in the widely used ISC Kea DHCP server poses a significant security risk to network infrastructure…
The Cybersecurity and Infrastructure Security Agency (CISA) unveiled a comprehensive Cybersecurity Advisory (CSA) designed to empower network defenders to detect,…