Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
Picture this scenario: Six months after celebrating their “zero trust transformation,” a financial services firm gets hit with a devastating…
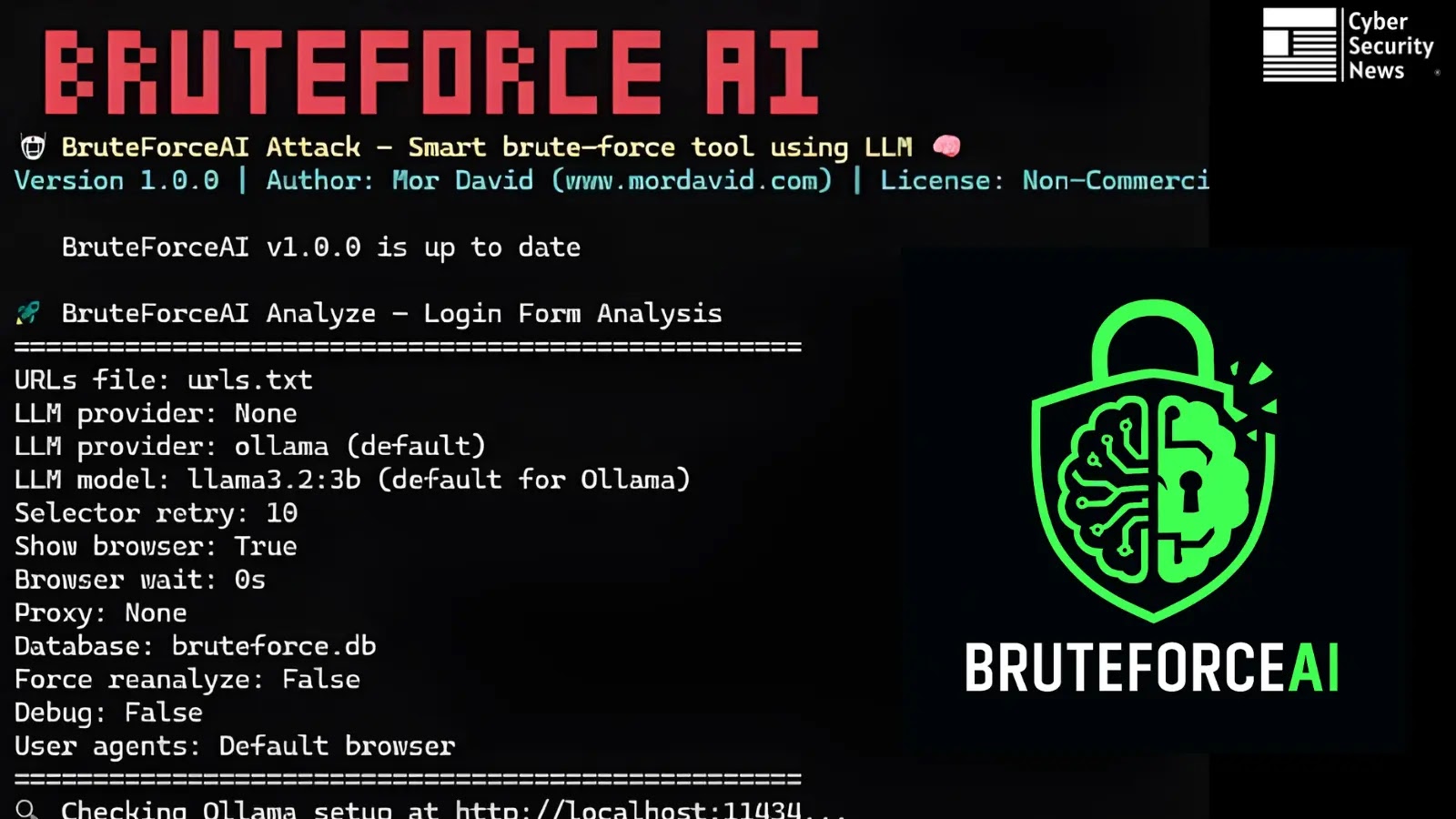
BruteForceAI, an innovative penetration testing framework developed by Mor David, integrates large language models (LLMs) with browser automation to autonomously…
The Underground ransomware gang has been coordinating recurring attacks on enterprises throughout the globe in a worrying increase in cyber…
A new report from Anthropic shows how criminals are using AI to actively run parts of their operations. The findings…
To reduce the number of harmful apps targeting Android users, Google has announced that certified Android devices will require all…
I’ve had a number of thoughts around Claude Code in the last couple of days. I’ve especially been trying to…
A newly observed variant of the Zip Slip vulnerability has emerged, enabling threat actors to exploit path traversal flaws in…
Nagios has addressed a significant cross-site scripting (XSS) vulnerability in its enterprise monitoring platform Nagios XI that could allow remote…
A critical vulnerability (CVE-2025-9074) in Docker Desktop for Windows and macOS was fixed. The flaw allowed a malicious container to…
27 Aug Next-Gen Security Awareness Training Series On The Cybercrime Magazine Podcast Posted at 09:16h in Blogs by Amanada Glassner…
A threat activity cluster known as ShadowSilk has been attributed to a fresh set of attacks targeting government entities within…