If you’re a Neovim user feeling left out watching everyone use Claude Code with VS Code, here’s my dead simple…
The Healthcare Services Group (HSGI) is alerting more than 600,000 individuals that their personal information was exposed in a security…
Spotify today rolled out a native direct messaging feature, Messages, for both Free and Premium users aged 16+ in select…
In a significant step to secure the defense industrial base (DIB), the Department of Defense (DoD) has officially released the…
NVIDIA released a security bulletin for NVIDIA® NeMo Curator addressing a high-severity vulnerability (CVE-2025-23307) that affects all prior versions of…
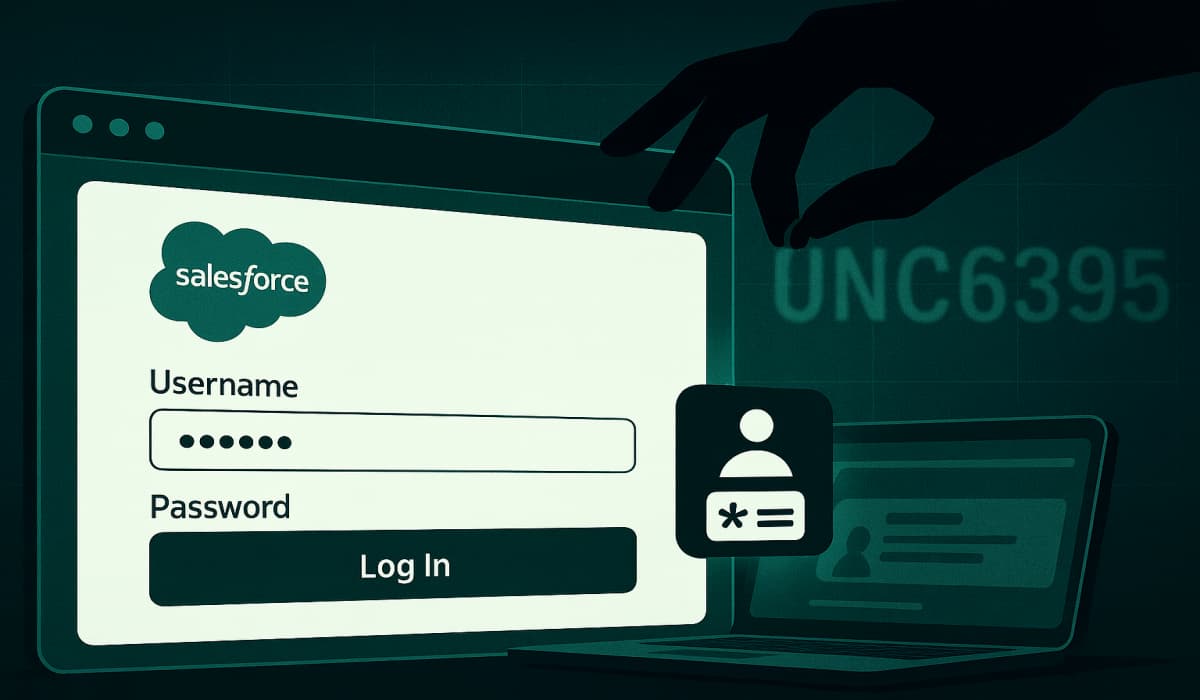
A new advisory from Google and Mandiant reveals a widespread data breach in Salesforce. Learn how UNC6395 bypassed MFA using…
27 Aug Next-Gen Security Awareness Training Series On The Cybercrime Magazine Podcast Posted at 09:16h in Blogs by Amanada Glassner…
TheTruthSpy is at it again. A security researcher has discovered a flaw in the Android-based stalkerware that allows anyone to…
The scariest thing to me about AI is that I think very few of the current companies and products that…
While such activity so far does not appear to be the norm across the ransomware ecosystem, the findings represent a…
The threat actor known as TAG-144, also referred to as Blind Eagle or APT-C-36, has been linked to five distinct…
Google has removed 77 malicious apps from the Google Play Store. Before they were removed, researchers at ThreatLabz discovered the…