Google has disclosed a critical zero-day vulnerability in the V8 JavaScript engine used by Chrome, tracked as CVE-2025-5419. Before a…
A critical security risk has emerged for Windows users of WhatsApp Desktop who also have Python installed. Attackers can exploit…
CVE-2025-48384, a recently patched vulnerability in the popular distributed revision control system Git, is being exploited by attackers. Details about…
Major French retail chain Auchan announced on August 21, 2025, that it suffered a significant cybersecurity incident resulting in the…
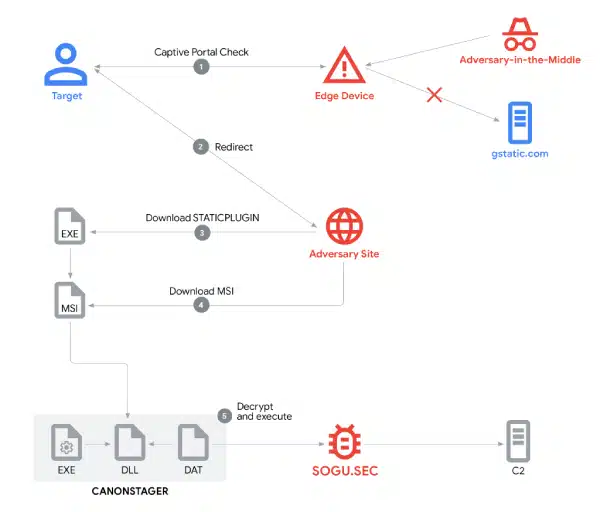
Google Threat Intelligence Group (GTIG) has uncovered a multifaceted cyber espionage operation attributed to the PRC-nexus threat actor UNC6384, believed…
Aug 26, 2025Ravie Lakshmanan Cybersecurity researchers have discovered a new variant of an Android banking trojan called HOOK that features…
Google’s Threat Intelligence Group has uncovered a cyber espionage campaign of a PRC-linked threat actor, which it tracks as UNC6384,…
U.S. CISA adds Citrix Session Recording, and Git flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini August 26, 2025 U.S….
A comprehensive analysis of the top 10 social media platforms reveals that X (formerly Twitter) stands out as the most…
Maryland’s transit network experienced widespread disruption this week after a sophisticated cyberattack targeted critical information systems, forcing the Maryland Transit…
Social media algorithms are pushing unsolicited pornographic content into children’s feeds, according to a report by the Children’s Commissioner. The…
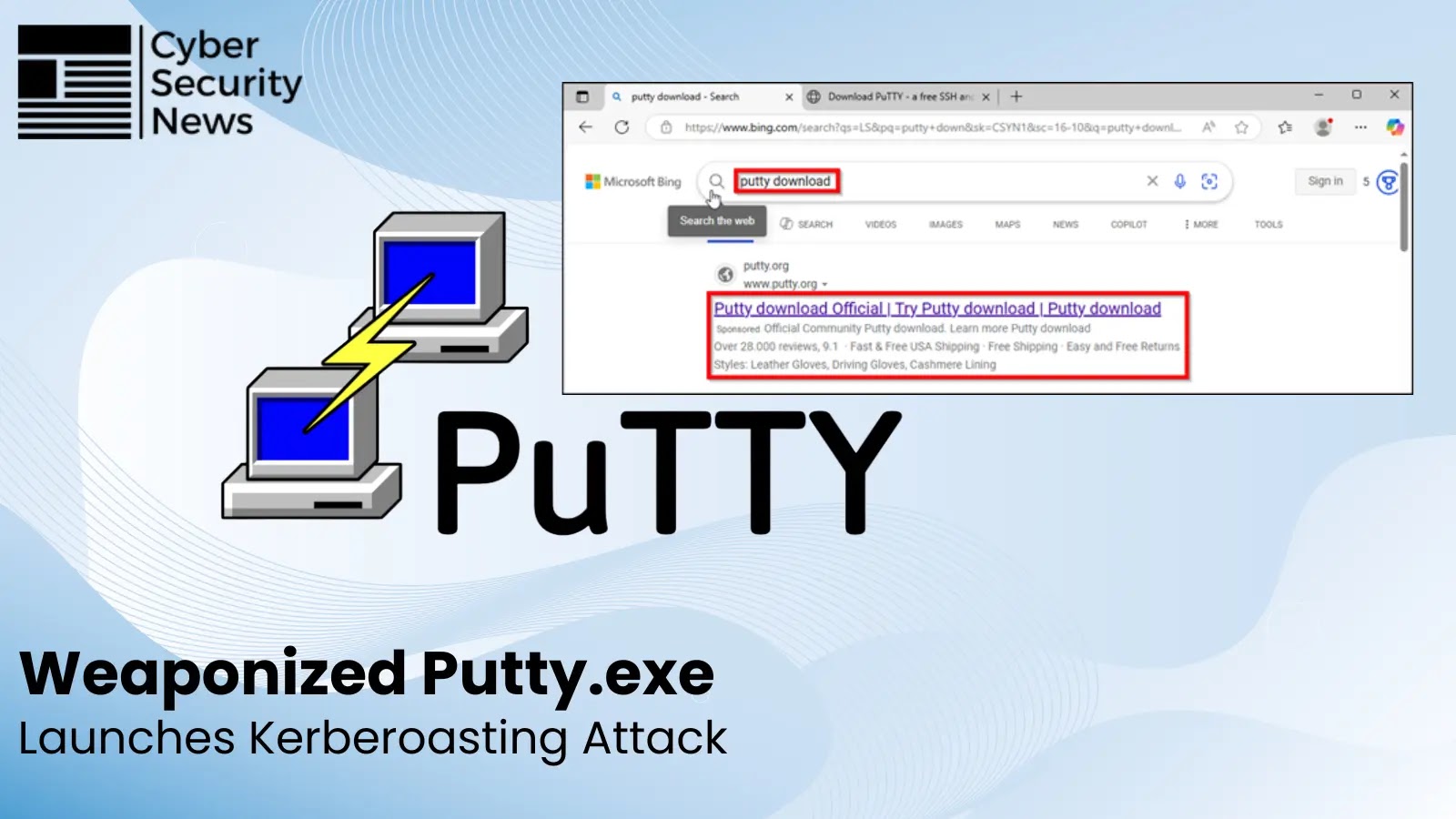
A malvertising campaign using sponsored results on Microsoft’s search platform delivered a weaponized PuTTY that established persistence, enabled hands-on keyboard…