The manufacturing sector is entering a new phase of digital transformation. According to Rockwell Automation’s 10th Annual State of Smart…
Last week on Malwarebytes Labs: Stay safe! We don’t just report on threats – we help protect your social media…
A cybersecurity researcher has unveiled a sophisticated new method for extracting Windows credentials and secrets that successfully evades detection by…
Satellites play a huge role in our daily lives, supporting everything from global communications to navigation, business, and national security….
A critical zero-click remote code execution vulnerability in Apple’s iOS has been disclosed with a working proof-of-concept exploit, marking another…
Insider threats are among the hardest attacks to detect because they come from people who already have legitimate access. Security…
A sophisticated malware strain known as KorPlug has emerged as a significant threat in the cybersecurity landscape, employing advanced obfuscation…
Salesforce has addressed multiple critical security vulnerabilities in Tableau Server and Desktop that could enable attackers to upload malicious files…
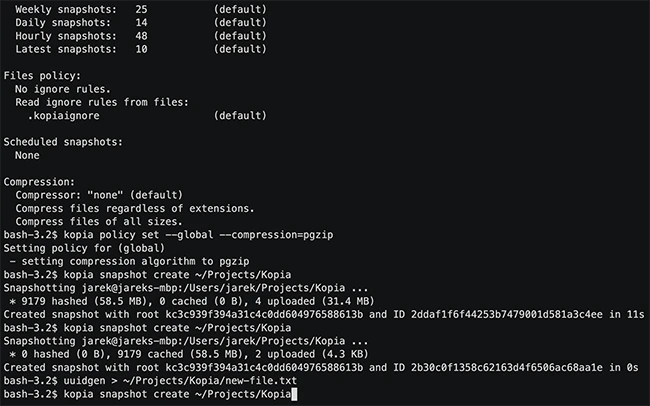
Kopia is an open-source backup and restore tool that lets you create encrypted snapshots of your files and store them…
Telstra’s digital health arm has won a $33.2 million contract to implement a new data architecture for the government’s My…
Adversarial AI Attacks, Mitigations, and Defense Strategies shows how AI systems can be attacked and how defenders can prepare. It’s…
Microsoft is rolling out a significant new administrative control feature in mid-September 2025 that will enable IT administrators to manage…