Cybersecurity researchers have developed an artificial intelligence system capable of automatically generating working exploits for published Common Vulnerabilities and Exposures…
Aug 22, 2025The Hacker NewsPenetration Testing / Security Operations Pentesting remains one of the most effective ways to identify real-world…
Unrestricted Resource Consumption (API4:2023) is the only threat category in the OWASP API Security Top 10 explicitly dedicated to Denial…
A critical vulnerability in Microsoft Azure’s API Connection infrastructure enabled attackers to compromise resources across different Azure tenants worldwide. The…
Cyber threat actors have launched sophisticated phishing operations aimed at military and government personnel in South Asia, leveraging defense-related lures…
Aug 22, 2025The Hacker NewsPenetration Testing / Security Operations Pentesting remains one of the most effective ways to identify real-world…
Law enforcement authorities in Africa have arrested over 1,200 suspects as part of ‘Operation Serengeti 2.0,’ an INTERPOL-led international crackdown…
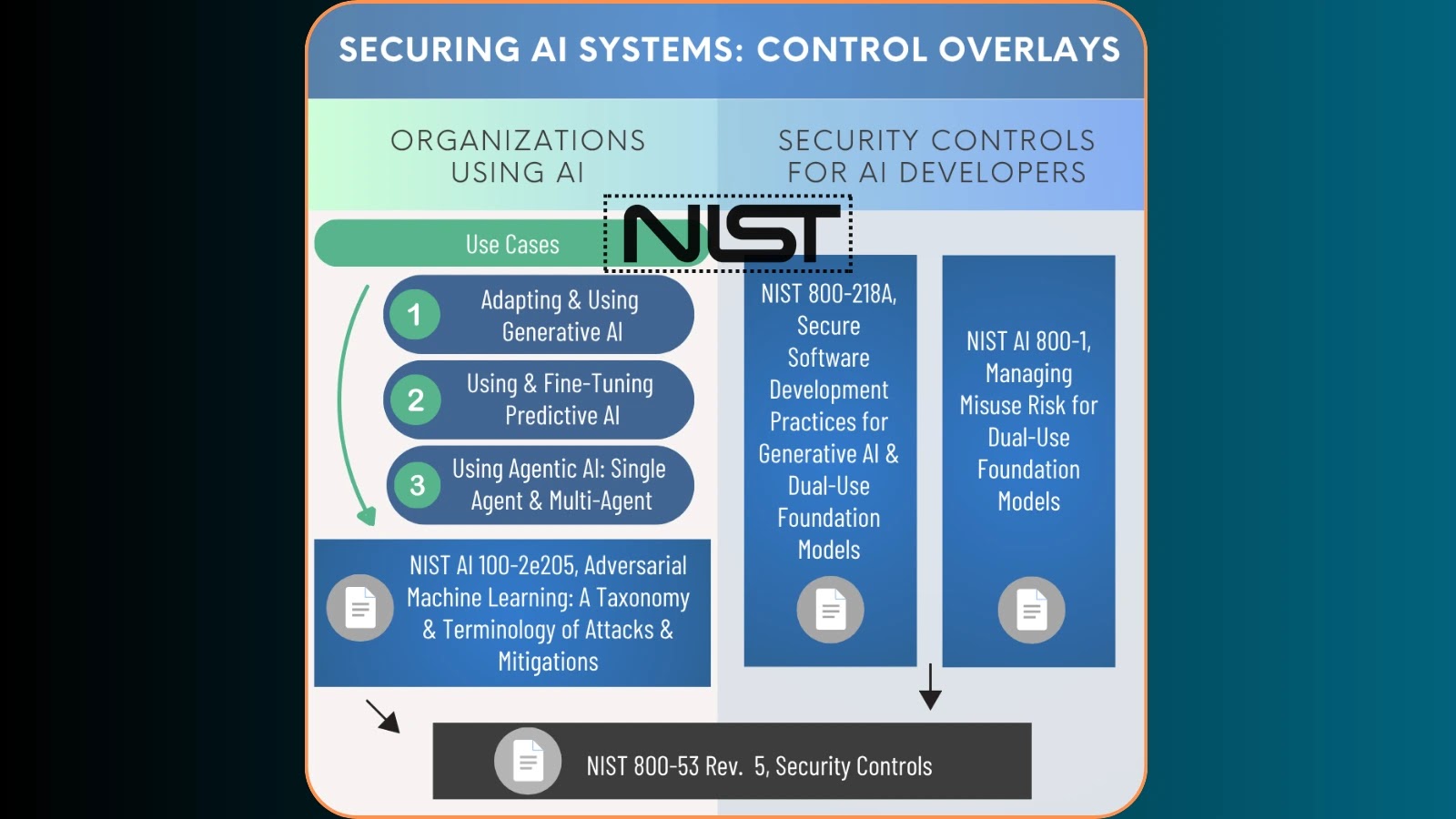
The National Institute of Standards and Technology (NIST) has unveiled a comprehensive concept paper outlining proposed NIST SP 800-53 Control…
A critical security vulnerability has been discovered in the widely-used sha.js npm package, exposing millions of applications to sophisticated hash…
Colt Discloses Breach After Warlock Ransomware Group Puts Files Up for Sale Pierluigi Paganini August 22, 2025 Colt Technology Services…
Kidney dialysis firm DaVita has confirmed that a ransomware gang that breached its network stole the personal and health information…
Telecommunications giant Colt Technology Services has confirmed that customer data was compromised in a sophisticated cyber attack that began on…