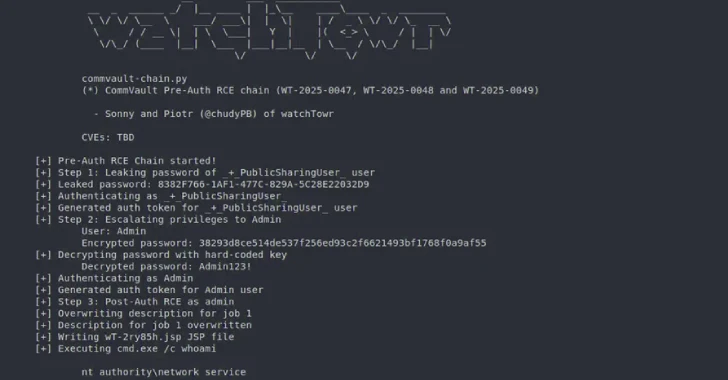
Aug 21, 2025Ravie LakshmananVulnerability / Software Security Commvault has released updates to address four security gaps that could be exploited…
Apple addressed the seventh actively exploited zero-day Pierluigi Paganini August 21, 2025 Apple addressed a vulnerability impacting iOS, iPadOS, and…
Mozilla has released Firefox 142 to address multiple high-severity security vulnerabilities that could allow attackers to execute arbitrary code remotely…
The week of August 4th, I had the opportunity to attend two exciting conferences in the cybersecurity world: Black Hat…
The Warlock ransomware group has intensified its operations by targeting unpatched on-premises Microsoft SharePoint servers, leveraging critical vulnerabilities to achieve…
Europol has confirmed that a widely reported $50,000 reward for information on the Qilin ransomware group is a “scam.” The…
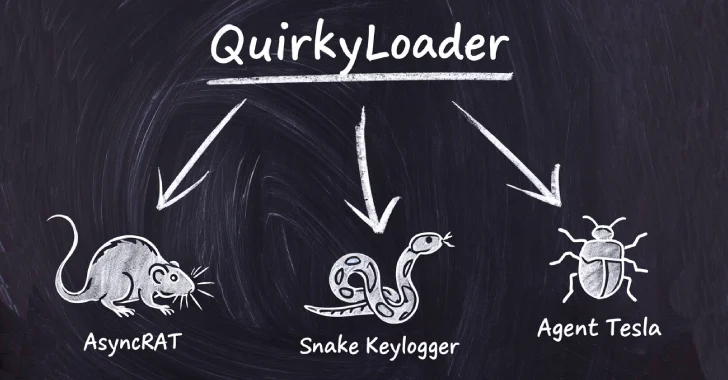
Aug 21, 2025Ravie LakshmananMalware / Email Security Cybersecurity researchers have disclosed details of a new malware loader called QuirkyLoader that’s…
The Home Office could be banned from unlawfully using computer algorithms to recommend whether migrants should be deported. Privacy International…
Hackers deploy DripDropper via Apache ActiveMQ flaw, patch systems to evade detection Pierluigi Paganini August 21, 2025 Hackers exploit Apache…
Europol has confirmed that a Telegram channel impersonating the agency and offering a $50,000 reward for information on two Qilin…
In recent weeks, the cybersecurity community has witnessed the rapid emergence of Warlock, a novel ransomware strain that weaponizes unpatched…
According to recent study by Research Nester, the global insider threat protection market Size was valued at USD 4 billion in 2023…