An Malicious actors are using reliable internet resources, such as the Internet Archive, more frequently to disseminate clandestine malware components…
The PromptFix attack tricks AI browsers with fake CAPTCHAs, leading them to phishing sites and fake stores where they auto-complete…
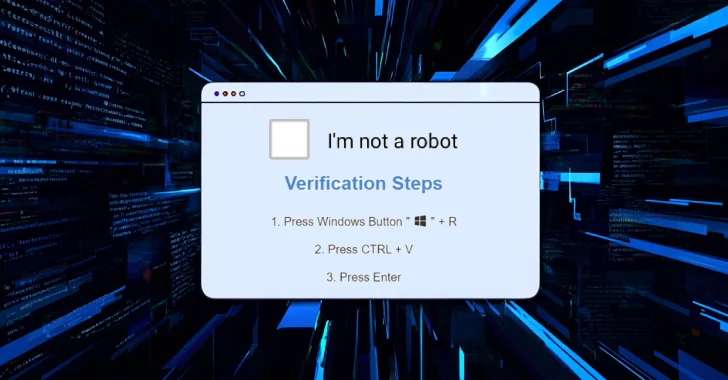
Aug 21, 2025Ravie LakshmananMalware / Cryptocurrency Threat actors have been observed leveraging the deceptive social engineering tactic known as ClickFix…
In mid-June 2025, Microsoft made an announcement about a suite of “Sovereign Cloud solutions” designed to ensure that data belonging…
Federal prosecutors on Tuesday charged an Oregon man with running a global botnet-for-hire operation called Rapper Bot that used hacked…
Cybersecurity researchers have observed a surge in phishing campaigns leveraging QR codes to deliver malicious payloads. This emerging threat, often…
According to recent study by Research Nester, the global insider threat protection market Size was valued at USD 4 billion in 2023…
Cyber spies associated with the threat actor group Paper Werewolf have demonstrated advanced capabilities in bypassing email security filters by…
The national police investigation into the Post Office Horizon scandal is expected to cost taxpayers more than £50m. Scandal victims…
A stealthy campaign emerged in early March 2025 that capitalized on a critical remote code execution flaw in GeoServer (CVE-2024-36401)…
A sophisticated spear-phishing campaign attributed to the Iranian-linked APT group MuddyWater is actively compromising CFOs and finance executives across Europe,…
A threat group linked to the Russian Federal Security Service’s (FSB) Center 16 unit has been compromising unpatched and end-of-life…