Security researchers at Imperva have disclosed a critical pre-handshake memory exhaustion vulnerability in the widely-used LSQUIC QUIC implementation that enables…
Aug 21, 2025Ravie LakshmananData Breach / Cybercrime A 20-year-old member of the notorious cybercrime gang known as Scattered Spider has…
Noah Michael Urban, a key member of the Scattered Spider cybercrime collective, was sentenced to 10 years in prison on…
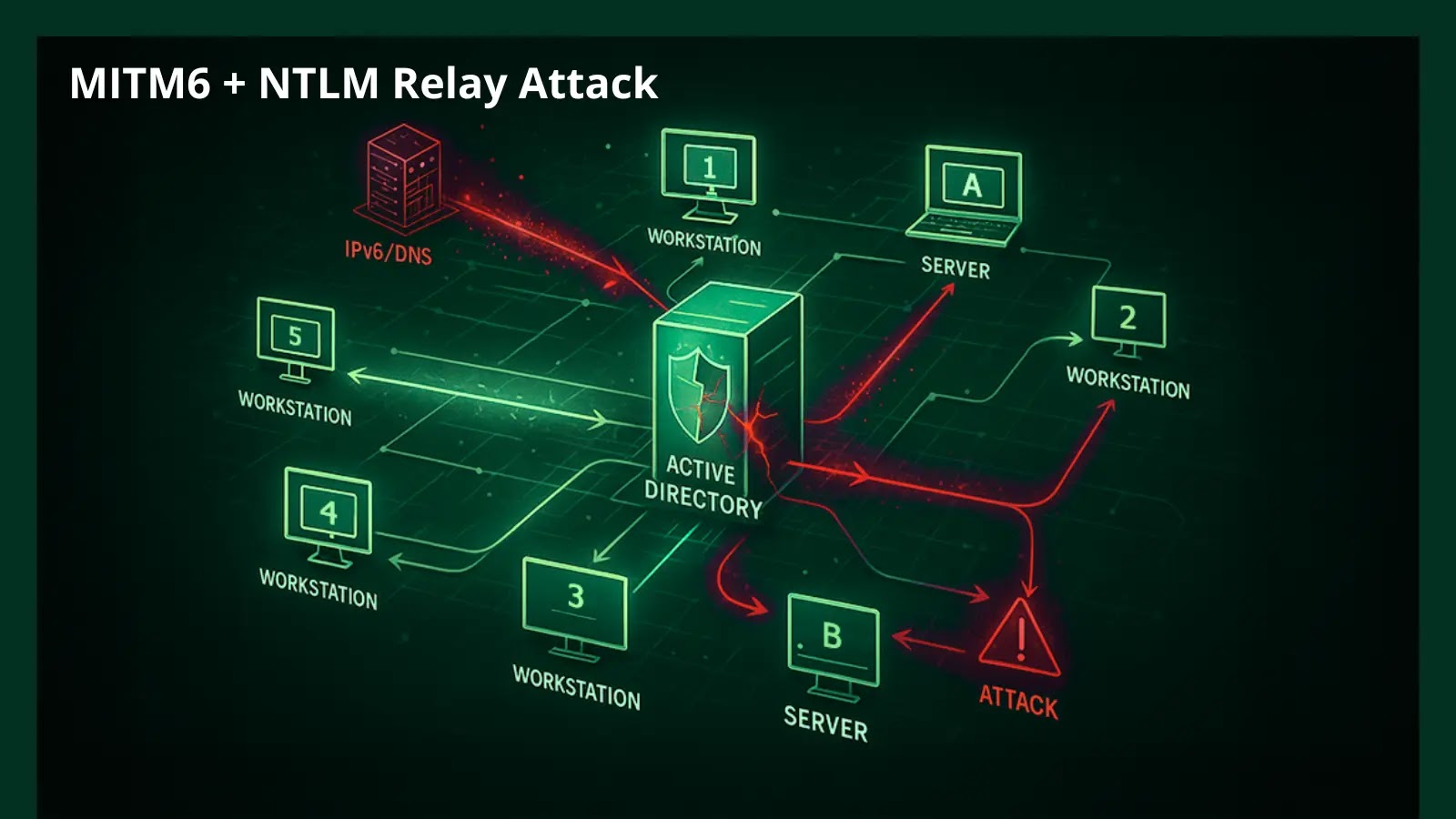
A sophisticated attack chain that combines MITM6 with NTLM relay techniques to achieve full Active Directory domain compromise. The attack…
FBI: Russia-linked group Static Tundra exploit old Cisco flaw for espionage Pierluigi Paganini August 21, 2025 FBI warns FSB-linked group…
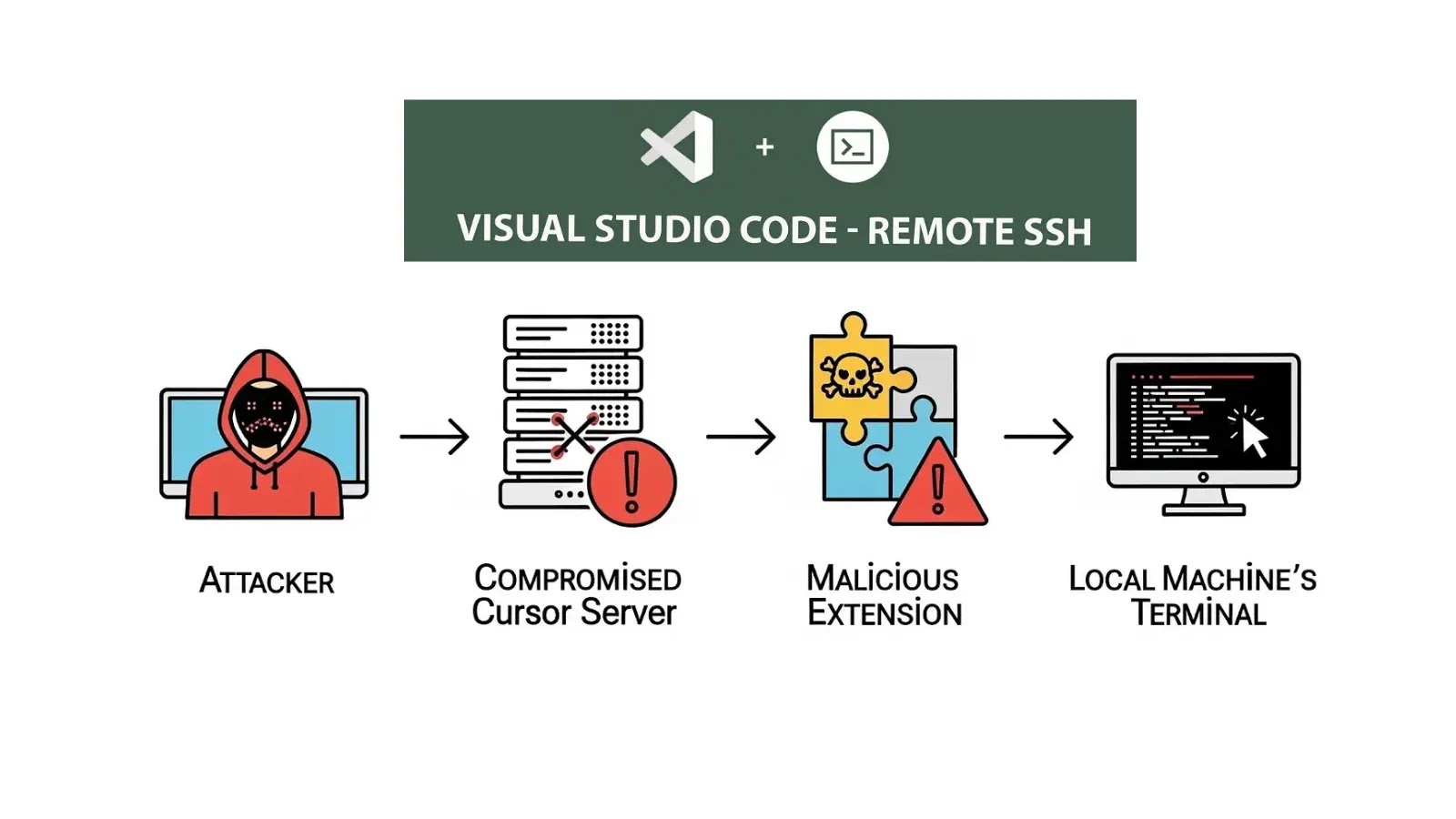
A critical security vulnerability has been discovered in Microsoft’s VS Code Remote-SSH extension that allows attackers to execute malicious code…
Federal authorities have charged a 22-year-old Oregon man with operating one of the most powerful distributed denial-of-service (DDoS) botnets ever…
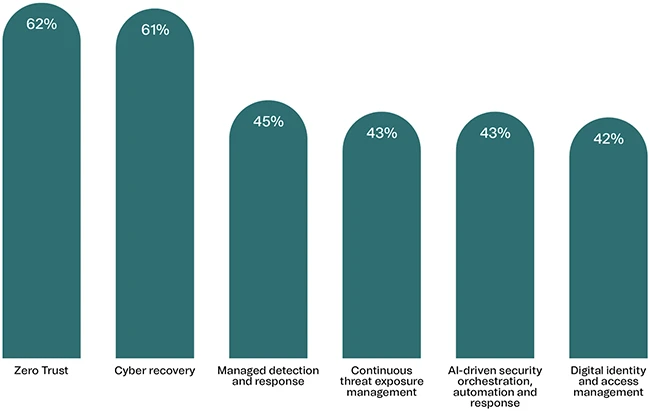
Organizations are increasing investments in cloud, AI, and emerging technologies, but their infrastructure and security strategies often lag behind. A…
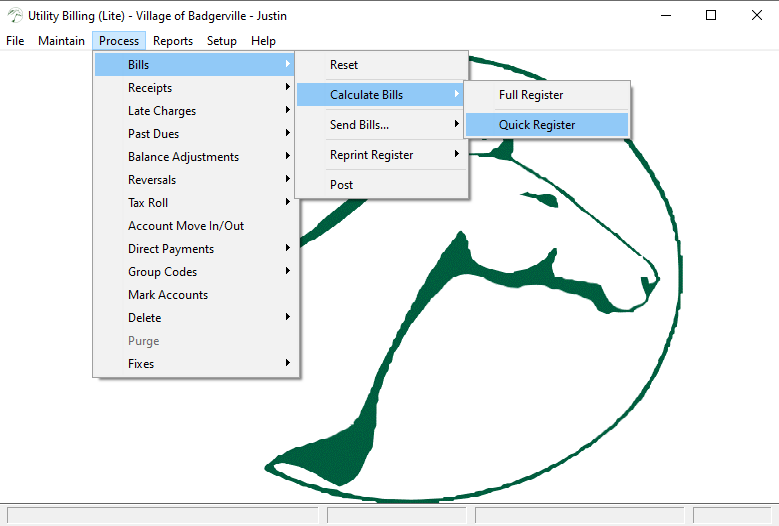
How often do you hear people talking about issues of legacy systems—especially in critical infrastructure environments? Here’s another example of…
Britain has dropped its demand for the iPhone maker Apple to provide a “backdoor” that would have enabled access to…
US CERT/CC warns of flaws in Workhorse Software accounting software used by hundreds of municipalities in Wisconsin Pierluigi Paganini August…
Orange Belgium, a subsidiary of telecommunications giant Orange Group, disclosed on Wednesday that attackers who breached its systems in July…