China’s Ministry of State Security accused the National Security Agency of conducting a yearslong attack on China’s national timekeeping infrastructure…
CISA says threat actors are now actively exploiting a high-severity Windows SMB privilege escalation vulnerability that can let them gain…
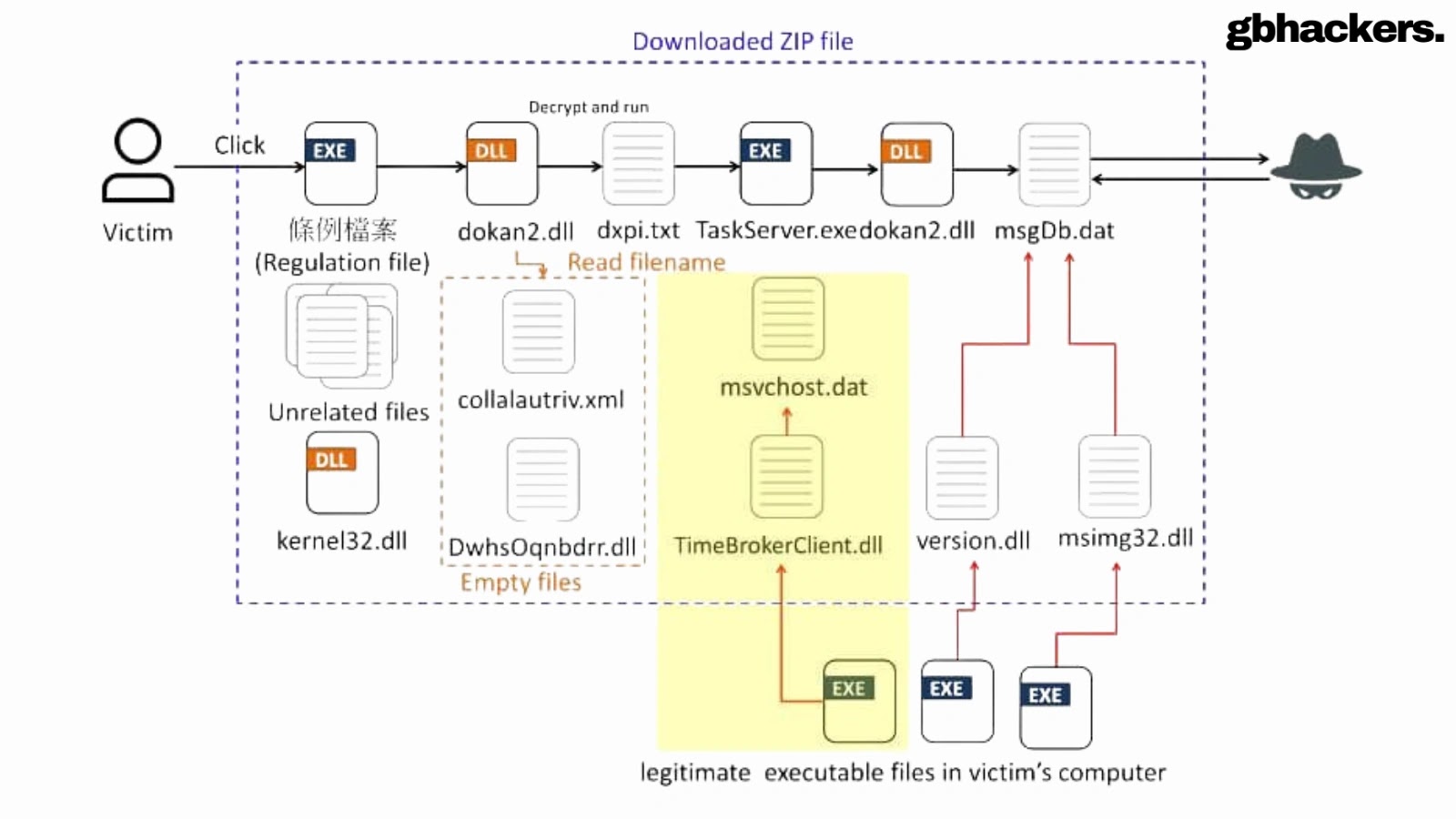
Security researchers are tracking a high-severity malware campaign that uses weaponized PDF files to distribute the Winos 4.0 malware. The…
This week on the Lock and Code podcast… Google is everywhere in our lives. It’s reach into our data extends…
A new and ongoing supply-chain attack is targeting developers on the OpenVSX and Microsoft Visual Studio marketplaces with self-spreading malware…
Moxa has fixed 5 vulnerabilities in its industrial network security appliances and routers, including a remotely exploitable flaw (CVE-2025-6950) that…
2026 is almost upon us, and with it comes a slate of must-attend cybersecurity conferences. Security experts from across sectors…
WhatsApp has won a ruling against spyware maker NSO Group forbidding it from targeting its users, while NSO Group in…
Microsoft is rolling out a fix for Active Directory issues affecting some Windows Server 2025 systems after installing security updates…
Network connectivity issues in AWS’ US-EAST-1 facility have caused widespread outages affecting thousands of websites along with some of the…
Cross-site scripting vulnerabilities are, by no doubt, one of the vulnerability types that’ll keep haunting applications for a long time….
Listen to the article 13 min This audio is auto-generated. Please let us know if you have feedback. Government agencies,…