For those of us who’ve tracked the ever-shifting landscape of cybersecurity, the narrative has always been one of escalating threats…
At the end of August, the AI company Anthropic announced that its chatbot Claude wouldn’t help anyone build a nuclear…
Salt Typhoon, the China-linked APT group that has a penchant for targeting telecommunications companies, has been spotted trying to sneak…
This week on the Lock and Code podcast… Google is everywhere in our lives. It’s reach into our data extends…
Atos has built additional UK delivery infrastructure, with a series of investments aimed to reassure customers their data is stored…
Cross-site scripting vulnerabilities are, by no doubt, one of the vulnerability types that’ll keep haunting applications for a long time….
Microsoft says the October 2025 Windows security updates are causing smart card authentication and certificate issues due to a change…
A massive cloud outage stemming from Amazon Web Services’s key US-EAST-1 region, its hub near the United States capitol in…
We regularly warn our readers about new scams and phishing texts. Almost everyone gets pestered with these messages. But where…
Oct 20, 2025Ravie LakshmananBrowser Security / Malware Cybersecurity researchers have uncovered a coordinated campaign that leveraged 131 rebranded clones of…
Amazon Web Services (AWS) said it is working to “fully restore” its customers’ cloud environments, after an “operational issue” within…
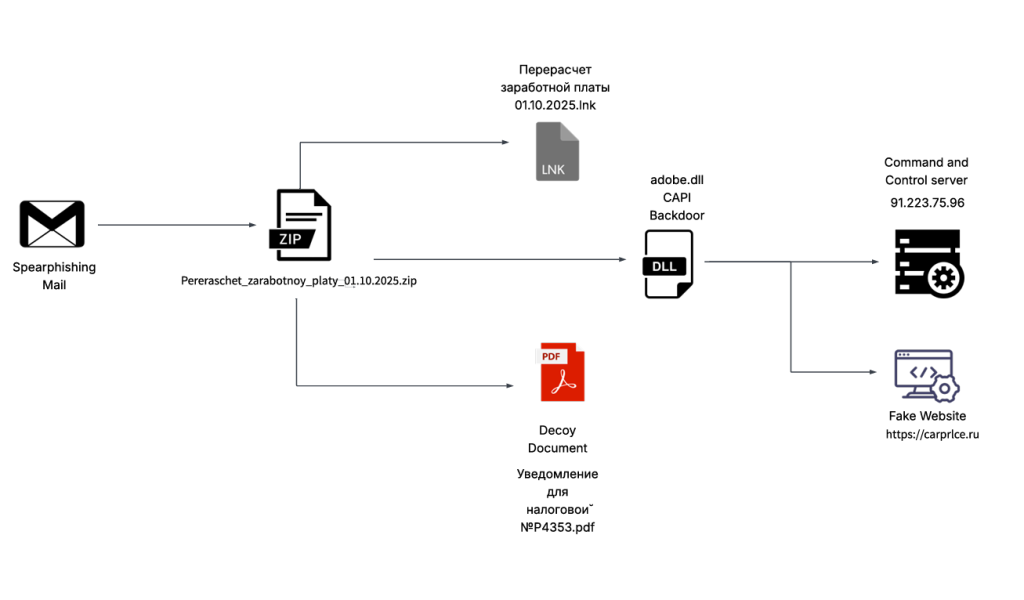
CAPI Backdoor targets Russia’s auto and e-commerce sectors Pierluigi Paganini October 20, 2025 A new campaign targets Russia’s auto and…