A sophisticated espionage campaign targeting diplomatic missions in South Korea has exposed the evolving tactics of North Korean state-sponsored hackers….
The Business Council of New York State, Inc., a prominent commercial organization based in Albany, has disclosed a data breach…
The Python Package Index (PyPI) has introduced new protections against domain resurrection attacks that enable hijacking accounts through password resets….
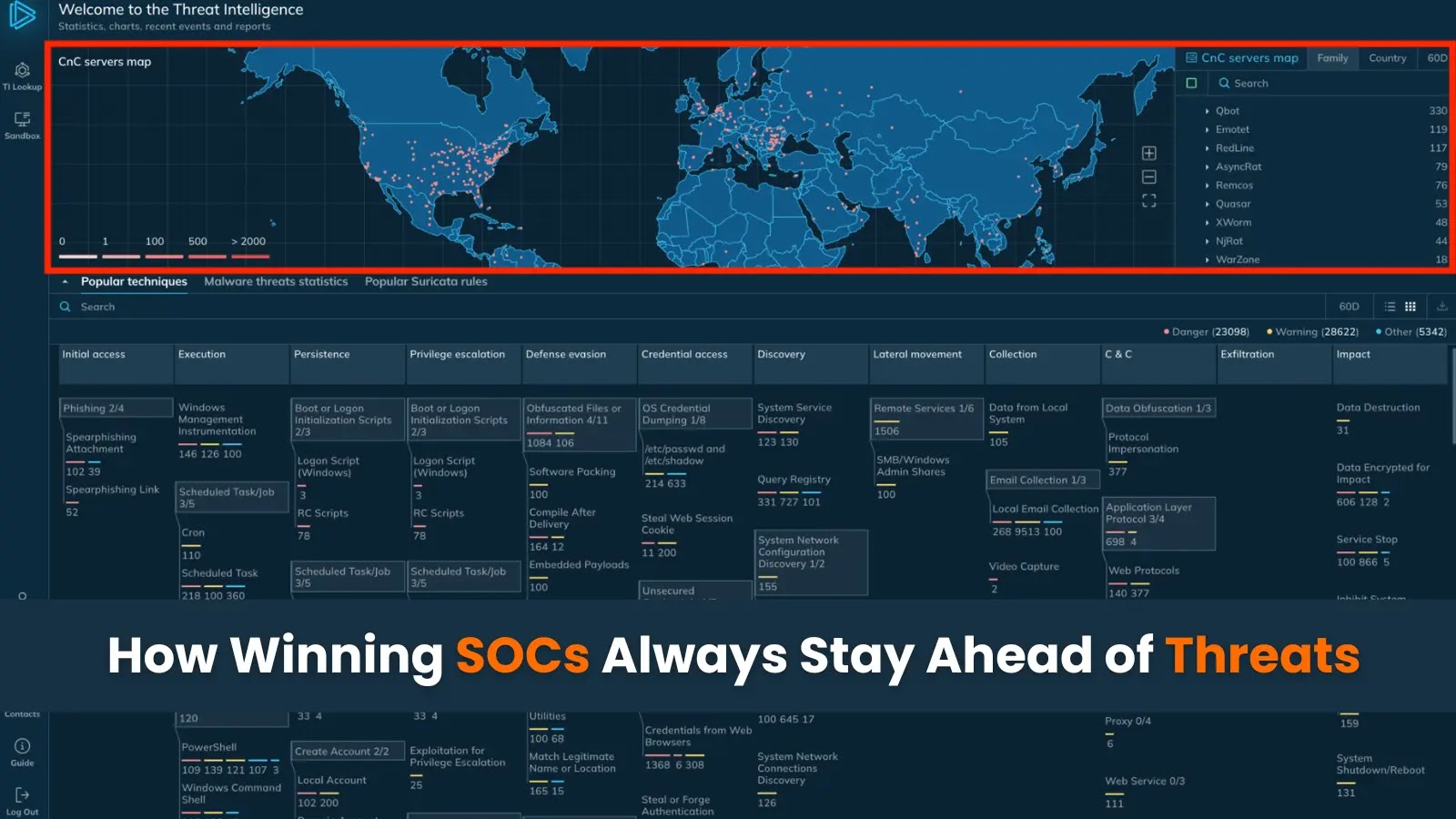
Despite the escalating danger of cybersecurity breaches, high-performing Security Operations Centers are able to maintain their resilience and prevent attacks….
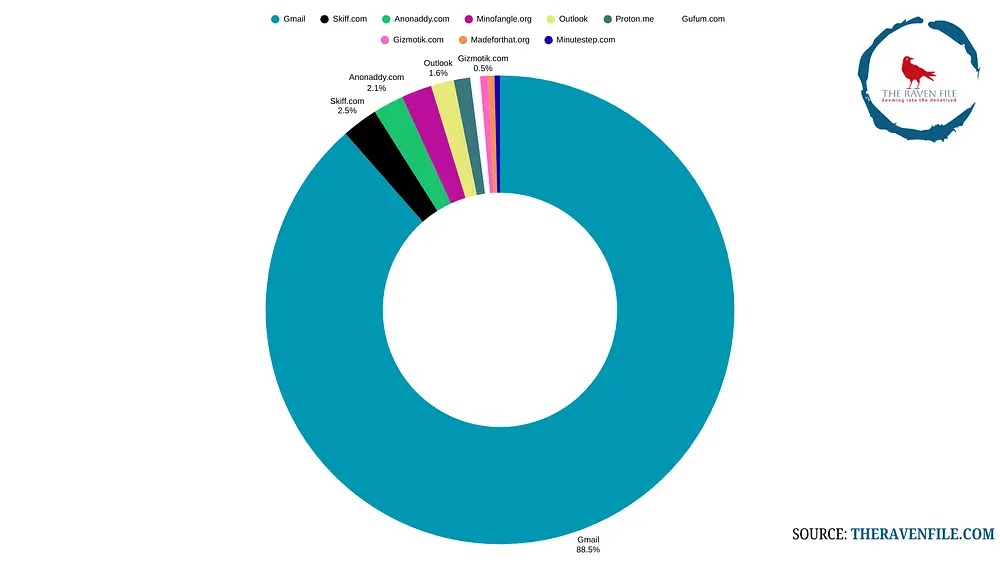
New cybersecurity research has revealed important details about how DPRK-affiliated IT professionals, who fall under Microsoft’s “Jasper Sleet” threat actor…
Microsoft is resolving a known issue that causes “couldn’t connect” errors when launching the Microsoft Teams desktop and web applications….
Recent cybersecurity intelligence has exposed a sophisticated infiltration campaign orchestrated by North Korean state-sponsored threat actors, specifically the Jasper Sleet…
Securing the Future of AI Powered Coding: Where Speed Meets Risk The rise of AI powered coding tools like Cursor and…
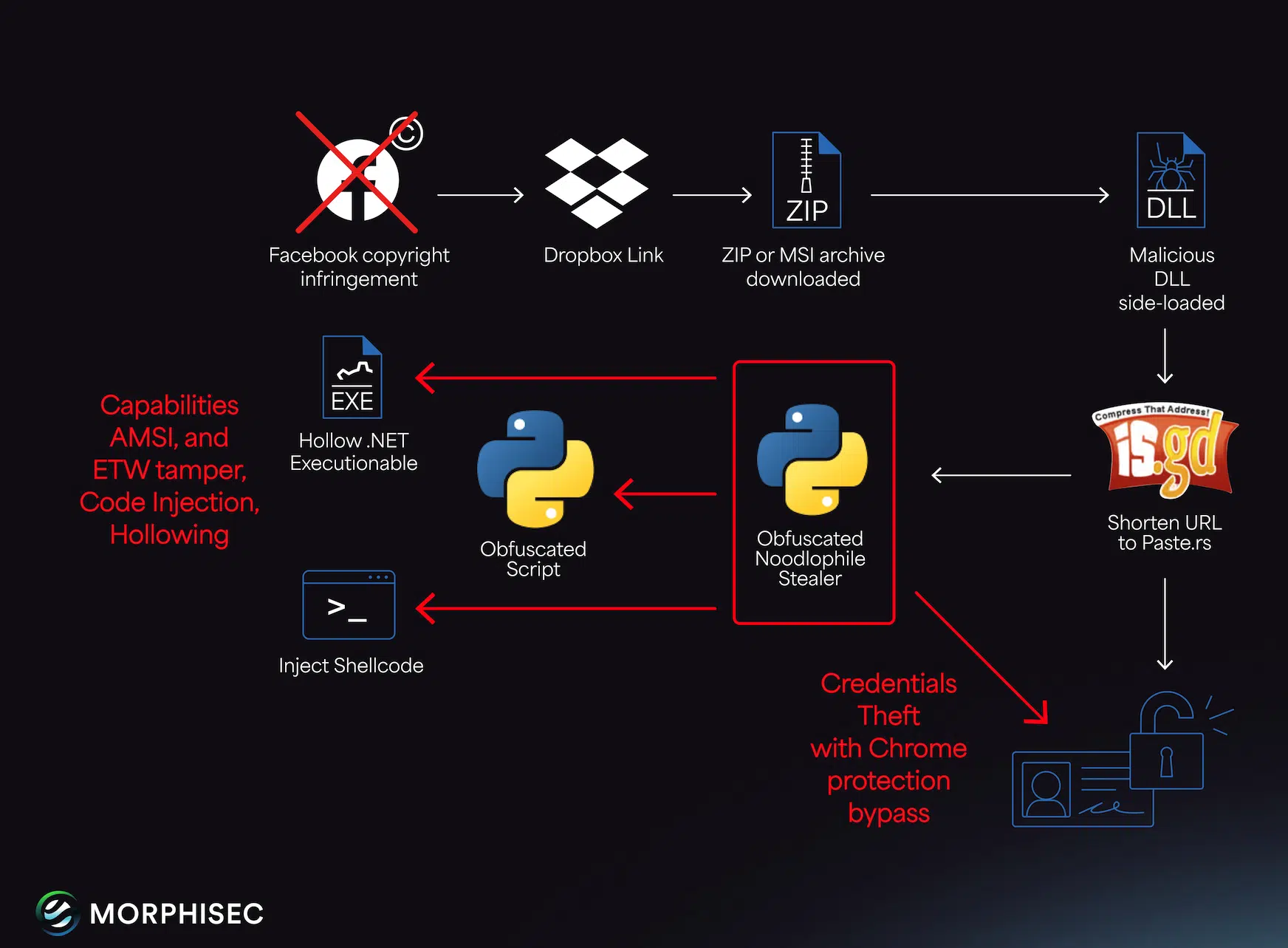
Noodlophile Stealer evolution Pierluigi Paganini August 19, 2025 Noodlophile malware spreads via copyright phishing, targeting firms in the U.S., Europe,…
Hong Kong police received more than 440,000 pieces of intelligence on cyberthreats targeting the city last year, while 5 per…
Okta has open-sourced ready-made Sigma-based queries for Auth0 customers to detect account takeovers, misconfigurations, and suspicious behavior in event logs….
A comprehensive security analysis has revealed alarming vulnerabilities affecting over 700 million users across multiple VPN applications, exposing critical flaws…