Colt Technology Services, a major UK-based telecommunications provider, continues to experience service disruptions following a serious cyberattack that began on…
China’s cyberspace regulator has summoned Nvidia to explain whether its H20 chips have any “back-door safety” risks, casting a shadow…
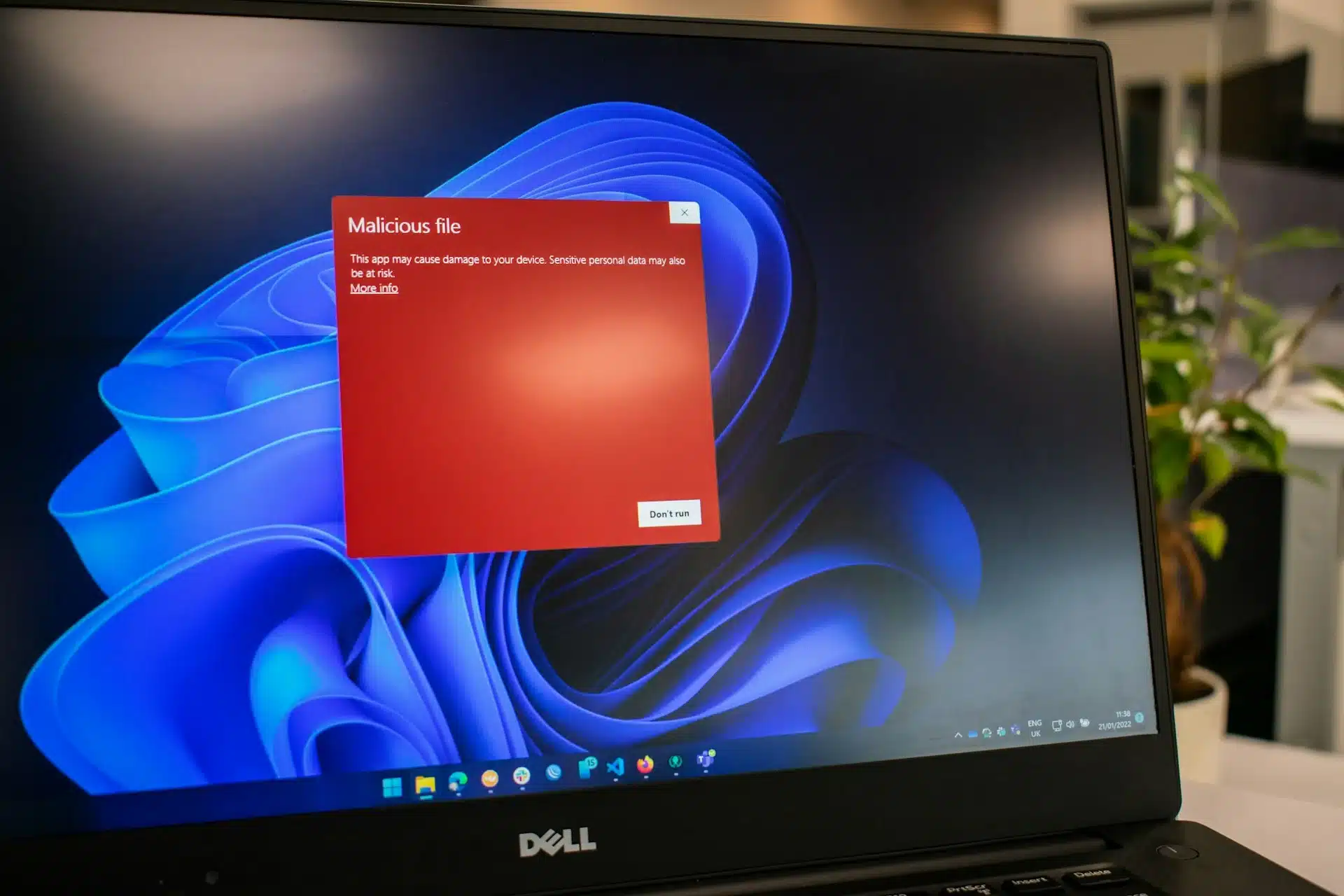
Microsoft has mitigated a known issue that caused Windows update failures when installing them from a network share using the…
The PostgreSQL Global Development Group has issued emergency security updates across all supported versions to address three critical vulnerabilities that…
WarLock ransomware claims breach at Colt and Hitachi, with Colt investigating and working to restore systems while experts review the…
Financial losses through cybersecurity crimes in Hong Kong hit HK$3.04 billion (US$387.3 million) in the first half of 2025, marking…
Use-after-free (UAF) vulnerabilities represent one of the most critical and prevalent security threats in modern software systems, particularly affecting applications…
Chinese-speaking cybercriminals are using ghost-tapping techniques to take advantage of Near Field Communication (NFC) relay tactics in a sophisticated evolution…
Aug 18, 2025The Hacker NewsData Breach / Regulatory Compliance Organizations handling various forms of sensitive data or personally identifiable information…
Expiration of a 2015 law at the end of September could dramatically reduce cyber threat information sharing within industry, as…
The alliance reflected the growing efforts in the country’s semiconductor industry and nascent AI sector to push forward Beijing’s tech…
A critical security vulnerability has been discovered in Rockwell Automation’s ControlLogix Ethernet communication modules, potentially allowing remote attackers to execute…