Workday, a California-based human resource and financial management service provider, disclosed last week that it was recently targeted in a…
On his visit to Beijing in July, Nvidia CEO Jensen Huang received a rock-star welcome as he announced to Chinese…
A significant security update rolled out by Microsoft with the Windows 11 24H2 (KB5063878) release is causing widespread issues for…
A critical vulnerability in Rockwell Automation’s ControlLogix Ethernet modules has been discovered that could allow remote attackers to execute malicious…
AI is moving from proof-of-concept into everyday security operations. In many SOCs, it is now used to cut down alert…
The PostgreSQL Global Development Group released emergency security updates on August 14, 2025, addressing three critical vulnerabilities that enable code…
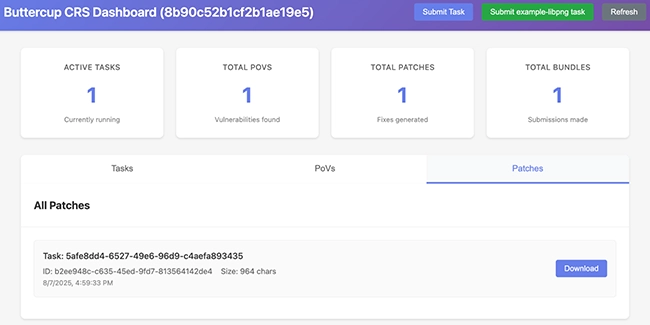
Buttercup is a free, automated, AI-powered platform that finds and fixes vulnerabilities in open-source software. Developed by Trail of Bits,…
As families across the country prepare for the return to school, cybercriminals are exploiting the seasonal rush with a fresh…
Prevention effectiveness is falling, detection gaps remain wide, and attackers are exploiting weaknesses in data protection and credentials. Data theft…
Google is facing Federal Court proceedings and a $55 million fine over historical agreements struck with Telstra and Optus to…
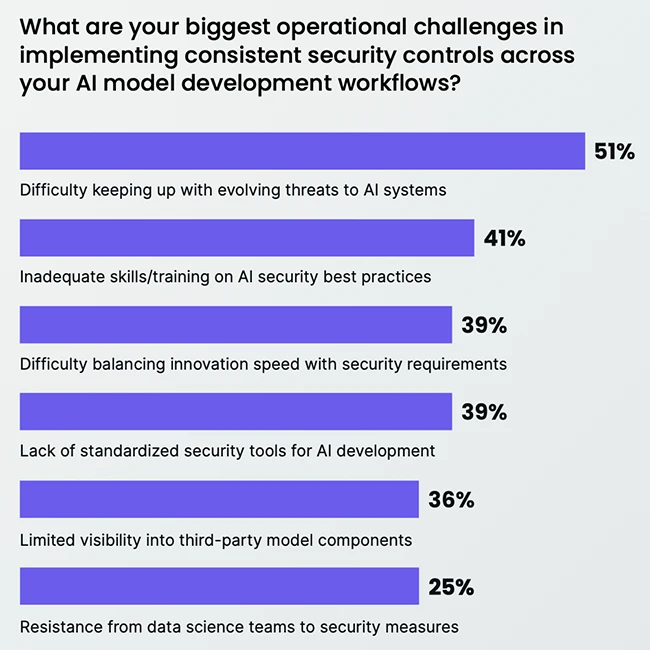
While most organizations understand the need for strong AI model governance, many are still struggling to close gaps that could…
Insurer IAG is using generative artificial intelligence to assess whether a property requires urgent repairs following a hazard or incident….