Cybersecurity researchers from watchTowr Labs have published a comprehensive technical analysis of a critical pre-authentication command injection vulnerability affecting Fortinet…
Aug 16, 2025Ravie LakshmananMalware / Vulnerability The threat actor known as EncryptHub is continuing to exploit a now-patched security flaw…
Here’s a different way to think about the change coming to the workforce and economy from AI. Imagine everyone in…
Palo Alto Networks has published an extensive malware analysis tutorial detailing the dissection of a sophisticated .NET-based threat that delivers…
The cybersecurity landscape faces a new sophisticated threat as the Crypto24 ransomware group demonstrates an alarming evolution in attack methodology,…
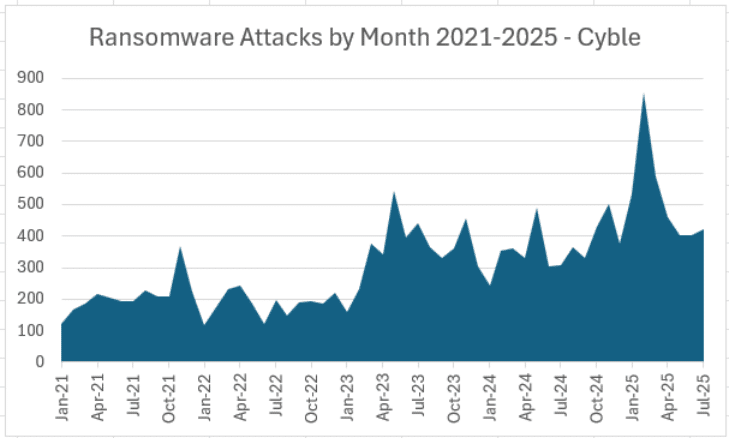
Qilin continues to stake a claim as the top ransomware group in the wake of the decline of RansomHub earlier…
Google Play has implemented comprehensive licensing requirements for cryptocurrency exchanges and software wallets, fundamentally reshaping the mobile app ecosystem for…
A federal district court declined to step in and review a combined $92 million fine imposed by the Federal Communications…
A sophisticated threat campaign has emerged that leverages CrossC2, an unofficial extension tool that expands Cobalt Strike’s notorious capabilities beyond…
Cybercriminal groups peddling sophisticated phishing kits that convert stolen card data into mobile wallets have recently shifted their focus to…
Cybercriminal groups peddling sophisticated phishing kits that convert stolen card data into mobile wallets have recently shifted their focus to…
New NFC-Driven Android Trojan PhantomCard targets Brazilian bank customers Pierluigi Paganini August 15, 2025 PhantomCard, an NFC-driven Android Trojan in Brazil,…