Cybercriminals are increasingly leveraging personalization tactics to enhance the effectiveness of their malware-delivery phishing campaigns, with threat actors customizing subject…
NIST has released a concept paper and proposed action plan for developing a series of NIST SP 800-53 Control Overlays for Securing…
Hackers exploit Microsoft flaw to breach Canada ’s House of Commons Pierluigi Paganini August 15, 2025 Hackers breached Canada ’s…
With 95% of enterprises facing incidents, Infosys research reveals a wide gap between AI adoption and responsible AI readiness, exposing…
The ransomware threat landscape witnessed a concerning surge in July 2025, with the Qilin ransomware group maintaining its dominant position…
I know AI is stupid because it can’t count the b’s in “blueberry” the same way I know Einstein was…
The cyberthreat landscape continues to evolve as malicious actors develop increasingly sophisticated attack methods, with the EncryptHub threat group emerging…
A sophisticated new variant of the FireWood backdoor has emerged, targeting Linux systems with enhanced evasion capabilities and streamlined command…
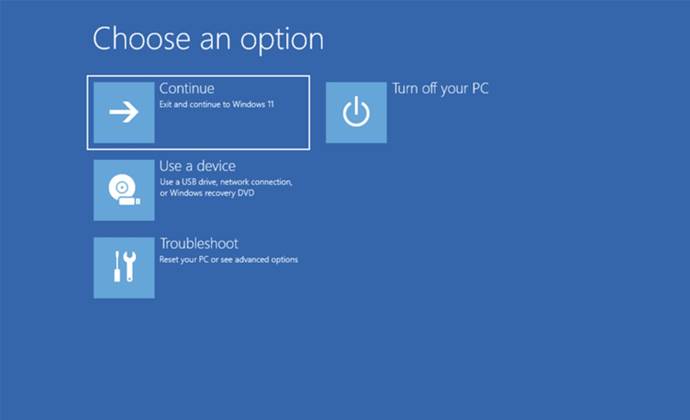
Microsoft’s own security researchers uncovered a set of of vulnerabilities in the Windows Recovery Environment (WinRE), one of which could…
Suncorp is “deep in delivery” of a new policy administration system in its AAMI brand in Australia, having first deployed…
U.S. officials imposed sanctions Thursday on Russian cryptocurrency exchange Garantex, its successor Grinex, and related affiliates, while also targeting its…
Operators behind the Crypto24 strain are employing highly coordinated, multi-stage attacks that blend legitimate system tools with bespoke malware to…