A detailed security guide released by Splunk to help cybersecurity teams detect and prevent ransomware attacks targeting ESXi infrastructure before…
The Cybersecurity and Infrastructure Security Agency (CISA), in partnership with eight other national cyber agencies, has released a comprehensive “Foundations…
14 Aug Fortune 500 CISO on Ransomware Incident Response Planning and Cyberinsurance Posted at 08:29h in Blogs by Taylor Fox…
Cybersecurity researchers have disclosed a new Android trojan called PhantomCard that abuses near-field communication (NFC) to conduct relay attacks for…
A sophisticated new threat vector has emerged that could undermine one of the most trusted authentication methods in cybersecurity. FIDO-based…
Microsoft has disclosed a critical security vulnerability in its Internet Information Services (IIS) Web Deploy tool that could allow attackers…
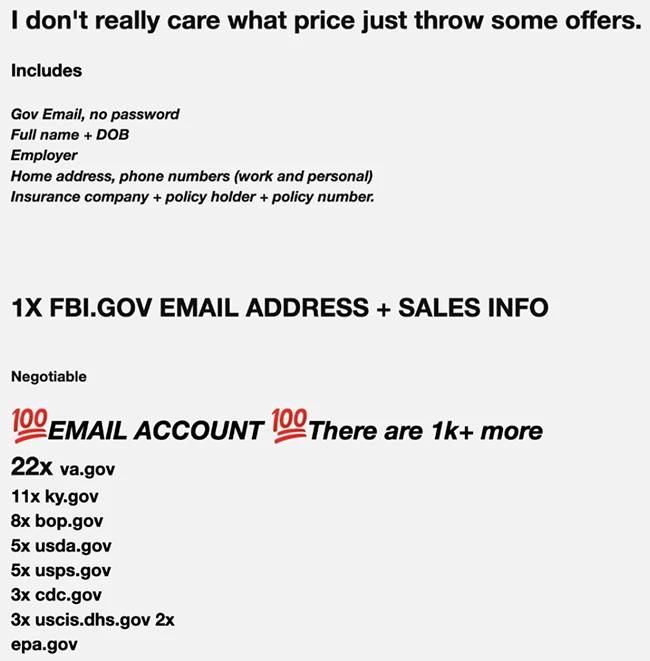
Active police and government email accounts are being sold on the dark web for as little as $40, giving cybercriminals…
You check that the windows are shut before leaving home. Return to the kitchen to verify that the oven and…
A critical security vulnerability has recently been discovered in certain versions of Zoom Clients for Windows that could expose users…
Critical vulnerabilities in Xerox FreeFlow Core, a widely-used print orchestration platform, allow unauthenticated remote attackers to execute malicious code on…
Trustwave SpiderLabs researchers have uncovered a sophisticated EncryptHub campaign that ingeniously abuses the Brave Support platform to deliver malicious payloads,…
The effectiveness of the European data protection framework depends on two essential pillars: robust individual rights and the institutional independence…